| Year | Number of missions |
|---|---|
| 1997 | 2
|
| 1998 | 1
|
| 1999 | 1
|
| 2000 | 1
|
| 2001 | 2
|
| 2002 | 2
|
| 2003 | 3
|
| 2004 | 5
|
| 2005 | 5
|
| 2006 | 6
|
| 2007 | 5
|
| 2008 | 6
|
| 2009 | 5
|
| 2010 | 5
|
| 2011 | 4
|
| 2012 | 5
|
| 2013 | 5
|
| 2014 | 7
|
| 2015 | 7
|
| 2016 | 8
|
| 2017 | 8
|
| 2018 | 9
|
| 2019 | 8
|
| 2020 | 8
|
| 2021 | 11
|
The planet Mars has been explored remotely by spacecraft. Probes sent from Earth, beginning in the late 20th century, have yielded a large increase in knowledge about the Martian system, focused primarily on understanding its geology and habitability potential. Engineering interplanetary journeys is complicated and the exploration of Mars has experienced a high failure rate, especially the early attempts. Roughly sixty percent of all spacecraft destined for Mars failed before completing their missions and some failed before their observations could begin. Some missions have been met with unexpected success, such as the twin Mars Exploration Rovers, Spirit and Opportunity, which operated for years beyond their specification.
Current status

As of December 2022, there are three operational rovers on the surface of Mars, the Curiosity and Perseverance rovers, both operated by the American space agency NASA, as well as the Zhurong rover, part of the Tianwen-1 mission by the China National Space Administration (CNSA). There are seven orbiters surveying the planet: Mars Odyssey, Mars Express, Mars Reconnaissance Orbiter, MAVEN, the Trace Gas Orbiter, the Hope Mars Mission, and the Tianwen-1 orbiter, which have contributed massive amounts of information about Mars. Various Mars sample return missions are being planned like NASA-ESA Mars Sample Return that will pick up the samples currently being collected by the Perseverance rover. In all, there are 11 probes currently surveying Mars including the Ingenuity helicopter, which is scouting sites for Perseverance to study.
The next missions expected to arrive at Mars are:
- The ExoMars program of ESA has delayed the launch of the Rosalind Franklin rover, until later in the 2020s.
- Mars Orbiter Mission 2 by India, planned launch in 2024.
Martian system
Mars has long been the subject of human interest. Early telescopic observations revealed color changes on the surface that were attributed to seasonal vegetation and apparent linear features were ascribed to intelligent design. Further telescopic observations found two moons, Phobos and Deimos, polar ice caps and the feature now known as Olympus Mons, the Solar System's tallest mountain. The discoveries piqued further interest in the study and exploration of the red planet. Mars is a rocky planet, like Earth, that formed around the same time, yet with only half the diameter of Earth, and a far thinner atmosphere; it has a cold and desert-like surface.
One way the surface of Mars has been categorized, is by thirty "quadrangles", with each quadrangle named for a prominent physiographic feature within that quadrangle.
Launch windows

The minimum-energy launch windows for a Martian expedition occur at intervals of approximately two years and two months (specifically 780 days, the planet's synodic period with respect to Earth). In addition, the lowest available transfer energy varies on a roughly 16-year cycle. For example, a minimum occurred in the 1969 and 1971 launch windows, rising to a peak in the late 1970s, and hitting another low in 1986 and 1988.
| Year | Window | Spacecraft (launched or planned) |
|---|---|---|
| 2013 | Nov | MAVEN, Mars Orbiter Mission |
| 2016 | Mar | ExoMars TGO |
| 2018 | May | InSight |
| 2020 | Jul–Sep | (1) Mars Hope orbiter, (2) Tianwen-1 orbiter, deployable and remote camera, lander and Zhurong rover (3) Mars 2020 Perseverance rover and Ingenuity helicopter |
| 2022 | Aug–Nov | none |
| 2024–25 | (1) Mars Orbiter Mission 2 (MOM-2) (2) Escape and Plasma Acceleration and Dynamics Explorer mission (EscaPADE) |
Past and current missions
| Decade |
|
|---|---|
| 1960s | 13
|
| 1970s | 11
|
| 1980s | 2
|
| 1990s | 8
|
| 2000s | 8
|
| 2010s | 6
|
| 2020s | 3
|
Starting in 1960, the Soviets launched a series of probes to Mars including the first intended flybys and hard (impact) landing (Mars 1962B). The first successful flyby of Mars was on 14–15 July 1965, by NASA's Mariner 4. On November 14, 1971, Mariner 9 became the first space probe to orbit another planet when it entered into orbit around Mars. The amount of data returned by probes increased dramatically as technology improved.
The first to contact the surface were two Soviet probes: Mars 2 lander on November 27 and Mars 3 lander on December 2, 1971—Mars 2 failed during descent and Mars 3 about twenty seconds after the first Martian soft landing. Mars 6 failed during descent but did return some corrupted atmospheric data in 1974. The 1975 NASA launches of the Viking program consisted of two orbiters, each with a lander that successfully soft landed in 1976. Viking 1 remained operational for six years, Viking 2 for three. The Viking landers relayed the first color panoramas of Mars.
The Soviet probes Phobos 1 and 2 were sent to Mars in 1988 to study Mars and its two moons, with a focus on Phobos. Phobos 1 lost contact on the way to Mars. Phobos 2, while successfully photographing Mars and Phobos, failed before it was set to release two landers to the surface of Phobos.
Mars has a reputation as a difficult space exploration target; just 25 of 55 missions through 2019, or 45.5%, have been fully successful, with a further three partially successful and partially failures. However, of the sixteen missions since 2001, twelve have been successful and eight of these are still operational.
Missions that ended prematurely after Phobos 1 and 2 (1988) include (see Probing difficulties section for more details):
- Mars Observer (launched in 1992)
- Mars 96 (1996)
- Mars Climate Orbiter (1999)
- Mars Polar Lander with Deep Space 2 (1999)
- Nozomi (2003)
- Beagle 2 (2003)
- Fobos-Grunt with Yinghuo-1 (2011)
- Schiaparelli lander (2016)
Following the 1993 failure of the Mars Observer orbiter, the NASA Mars Global Surveyor achieved Mars orbit in 1997. This mission was a complete success, having finished its primary mapping mission in early 2001. Contact was lost with the probe in November 2006 during its third extended program, spending exactly 10 operational years in space. The NASA Mars Pathfinder, carrying a robotic exploration vehicle Sojourner, landed in the Ares Vallis on Mars in the summer of 1997, returning many images.

Legend: Active (white lined, ※) • Inactive • Planned (dash lined, ⁂)

NASA's Mars Odyssey orbiter entered Mars orbit in 2001. Odyssey's Gamma Ray Spectrometer detected significant amounts of hydrogen in the upper metre or so of regolith on Mars. This hydrogen is thought to be contained in large deposits of water ice.
The Mars Express mission of the European Space Agency (ESA) reached Mars in 2003. It carried the Beagle 2 lander, which was not heard from after being released and was declared lost in February 2004. Beagle 2 was located in January 2015 by HiRise camera on NASA's Mars Reconnaissance Orbiter (MRO) having landed safely but failed to fully deploy its solar panels and antenna. In early 2004, the Mars Express Planetary Fourier Spectrometer team announced the orbiter had detected methane in the Martian atmosphere, a potential biosignature. ESA announced in June 2006 the discovery of aurorae on Mars by the Mars Express.
In January 2004, the NASA twin Mars Exploration Rovers named Spirit (MER-A) and Opportunity (MER-B) landed on the surface of Mars. Both have met and exceeded all their science objectives. Among the most significant scientific returns has been conclusive evidence that liquid water existed at some time in the past at both landing sites. Martian dust devils and windstorms have occasionally cleaned both rovers' solar panels, and thus increased their lifespan. Spirit rover (MER-A) was active until 2010, when it stopped sending data because it got stuck in a sand dune and was unable to reorient itself to recharge its batteries.
On 10 March 2006, NASA's Mars Reconnaissance Orbiter (MRO) probe arrived in orbit to conduct a two-year science survey. The orbiter began mapping the Martian terrain and weather to find suitable landing sites for upcoming lander missions. The MRO captured the first image of a series of active avalanches near the planet's north pole in 2008.
Rosetta came within 250 km of Mars during its 2007 flyby. Dawn flew by Mars in February 2009 for a gravity assist on its way to investigate Vesta and Ceres.
Phoenix landed on the north polar region of Mars on May 25, 2008. Its robotic arm dug into the Martian soil and the presence of water ice was confirmed on June 20, 2008. The mission concluded on November 10, 2008, after contact was lost. In 2008, the price of transporting material from the surface of Earth to the surface of Mars was approximately US$309,000 per kilogram.
The Mars Science Laboratory mission was launched on November 26, 2011, and it delivered the Curiosity rover on the surface of Mars on August 6, 2012 UTC. It is larger and more advanced than the Mars Exploration Rovers, with a velocity of up to 90 meters per hour (295 feet per hour).[38] Experiments include a laser chemical sampler that can deduce the composition of rocks at a distance of 7 meters.

MAVEN orbiter was launched on 18 November 2013, and on 22 September 2014, it was injected into an areocentric elliptic orbit 6,200 km (3,900 mi) by 150 km (93 mi) above the planet's surface to study its atmosphere. Mission goals include determining how the planet's atmosphere and water, presumed to have once been substantial, were lost over time.
The Indian Space Research Organisation (ISRO) launched their Mars Orbiter Mission (MOM) on November 5, 2013, and it was inserted into Mars orbit on September 24, 2014. India's ISRO is the fourth space agency to reach Mars, after the Soviet space program, NASA and ESA. India successfully placed a spacecraft into Mars orbit, and became the first country to do so in its maiden attempt.
The ExoMars Trace Gas Orbiter arrived at Mars in 2016 and deployed the Schiaparelli EDM lander, a test lander. Schiaparelli crashed on surface, but it transmitted key data during its parachute descent, so the test was declared a partial success.
Overview of missions
The following entails a brief overview of Mars exploration, oriented towards orbiters and flybys; see also Mars landing and Mars rover.
Early Soviet missions
1960s

Between 1960 and 1969, the Soviet Union launched nine probes intended to reach Mars. They all failed: three at launch; three failed to reach near-Earth orbit; one during the burn to put the spacecraft into trans-Mars trajectory; and two during the interplanetary orbit.
The Mars 1M programs (sometimes dubbed Marsnik in Western media) was the first Soviet uncrewed spacecraft interplanetary exploration program, which consisted of two flyby probes launched towards Mars in October 1960, Mars 1960A and Mars 1960B (also known as Korabl 4 and Korabl 5 respectively). After launch, the third stage pumps on both launchers were unable to develop enough pressure to commence ignition, so Earth parking orbit was not achieved. The spacecraft reached an altitude of 120 km before reentry.
Mars 1962A was a Mars flyby mission, launched on October 24, 1962, and Mars 1962B an intended first Mars lander mission, launched in late December of the same year (1962). Both failed from either breaking up as they were going into Earth orbit or having the upper stage explode in orbit during the burn to put the spacecraft into trans-Mars trajectory.
The first success
| Spacecraft | Orbiter or flyby outcome | Lander outcome |
|---|---|---|
| Mars 1 | Failure | Failure |
| Mars 2 | Success | Failure |
| Mars 3 | Partial success | Partial success |
| Mars 4 | Failure | — |
| Mars 5 | Partial success | — |
| Mars 6 | Success | Failure |
| Mars 7 | Success | Failure |
| Phobos 1 | Failure | Not deployed |
| Phobos 2 | Partial success | Not deployed |
Mars 1 (1962 Beta Nu 1), an automatic interplanetary spacecraft launched to Mars on November 1, 1962, was the first probe of the Soviet Mars probe program to achieve interplanetary orbit. Mars 1 was intended to fly by the planet at a distance of about 11,000 km and take images of the surface as well as send back data on cosmic radiation, micrometeoroid impacts and Mars' magnetic field, radiation environment, atmospheric structure, and possible organic compounds. Sixty-one radio transmissions were held, initially at 2-day intervals and later at 5-day intervals, from which a large amount of interplanetary data was collected. On 21 March 1963, when the spacecraft was at a distance of 106,760,000 km from Earth, on its way to Mars, communications ceased due to failure of its antenna orientation system.
In 1964, both Soviet probe launches, of Zond 1964A on June 4, and Zond 2 on November 30, (part of the Zond program), resulted in failures. Zond 1964A had a failure at launch, while communication was lost with Zond 2 en route to Mars after a mid-course maneuver, in early May 1965.
In 1969, and as part of the Mars probe program, the Soviet Union prepared two identical 5-ton orbiters called M-69, dubbed by NASA as Mars 1969A and Mars 1969B. Both probes were lost in launch-related complications with the newly developed Proton rocket.
1970s
The USSR intended to have the first artificial satellite of Mars beating the planned American Mariner 8 and Mariner 9 Mars orbiters. In May 1971, one day after Mariner 8 malfunctioned at launch and failed to reach orbit, Cosmos 419 (Mars 1971C), a heavy probe of the Soviet Mars program M-71, also failed to launch. This spacecraft was designed as an orbiter only, while the next two probes of project M-71, Mars 2 and Mars 3, were multipurpose combinations of an orbiter and a lander with small skis-walking rovers that would be the first planet rovers outside the Moon. They were successfully launched in mid-May 1971 and reached Mars about seven months later. On November 27, 1971, the lander of Mars 2 crash-landed due to an on-board computer malfunction and became the first man-made object to reach the surface of Mars. On 2 December 1971, the Mars 3 lander became the first spacecraft to achieve a soft landing, but its transmission was interrupted after 14.5 seconds.
The Mars 2 and 3 orbiters sent back a relatively large volume of data covering the period from December 1971 to March 1972, although transmissions continued through to August. By 22 August 1972, after sending back data and a total of 60 pictures, Mars 2 and 3 concluded their missions. The images and data enabled creation of surface relief maps, and gave information on the Martian gravity and magnetic fields.
In 1973, the Soviet Union sent four more probes to Mars: the Mars 4 and Mars 5 orbiters and the Mars 6 and Mars 7 flyby/lander combinations. All missions except Mars 7 sent back data, with Mars 5 being most successful. Mars 5 transmitted just 60 images before a loss of pressurization in the transmitter housing ended the mission. Mars 6 lander transmitted data during descent, but failed upon impact. Mars 4 flew by the planet at a range of 2200 km returning one swath of pictures and radio occultation data, which constituted the first detection of the nightside ionosphere on Mars. Mars 7 probe separated prematurely from the carrying vehicle due to a problem in the operation of one of the onboard systems (attitude control or retro-rockets) and missed the planet by 1,300 kilometres (8.7×10−6 au).
Mariner program

In 1964, NASA's Jet Propulsion Laboratory made two attempts at reaching Mars. Mariner 3 and Mariner 4 were identical spacecraft designed to carry out the first flybys of Mars. Mariner 3 was launched on November 5, 1964, but the shroud encasing the spacecraft atop its rocket failed to open properly, dooming the mission. Three weeks later, on November 28, 1964, Mariner 4 was launched successfully on a 71⁄2-month voyage to Mars.
Mariner 4 flew past Mars on July 14, 1965, providing the first close-up photographs of another planet. The pictures, gradually played back to Earth from a small tape recorder on the probe, showed impact craters. It provided radically more accurate data about the planet; a surface atmospheric pressure of about 1% of Earth's and daytime temperatures of −100 °C (−148 °F) were estimated. No magnetic field or Martian radiation belts were detected. The new data meant redesigns for then planned Martian landers, and showed life would have a more difficult time surviving there than previously anticipated.

NASA continued the Mariner program with another pair of Mars flyby probes, Mariner 6 and 7. They were sent at the next launch window, and reached the planet in 1969. During the following launch window the Mariner program again suffered the loss of one of a pair of probes. Mariner 9 successfully entered orbit about Mars, the first spacecraft ever to do so, after the launch time failure of its sister ship, Mariner 8. When Mariner 9 reached Mars in 1971, it and two Soviet orbiters (Mars 2 and Mars 3) found that a planet-wide dust storm was in progress. The mission controllers used the time spent waiting for the storm to clear to have the probe rendezvous with, and photograph, Phobos. When the storm cleared sufficiently for Mars' surface to be photographed by Mariner 9, the pictures returned represented a substantial advance over previous missions. These pictures were the first to offer more detailed evidence that liquid water might at one time have flowed on the planetary surface. They also finally discerned the true nature of many Martian albedo features. For example, Nix Olympica was one of only a few features that could be seen during the planetary duststorm, revealing it to be the highest mountain (volcano, to be exact) on any planet in the entire Solar System, and leading to its reclassification as Olympus Mons.
Viking program
The Viking program launched Viking 1 and Viking 2 spacecraft to Mars in 1975; The program consisted of two orbiters and two landers – these were the second and third spacecraft to successfully land on Mars.
|
Martian sunset over Chryse Planitia at Viking 1 site (August 20, 1976) |
The primary scientific objectives of the lander mission were to search for biosignatures and observe meteorologic, seismic and magnetic properties of Mars. The results of the biological experiments on board the Viking landers remain inconclusive, with a reanalysis of the Viking data published in 2012 suggesting signs of microbial life on Mars.
|
|
The Viking orbiters revealed that large floods of water carved deep valleys, eroded grooves into bedrock, and traveled thousands of kilometers. Areas of branched streams, in the southern hemisphere, suggest that rain once fell.
Mars Pathfinder, Sojourner rover

Mars Pathfinder was a U.S. spacecraft that landed a base station with a roving probe on Mars on July 4, 1997. It consisted of a lander and a small 10.6-kilogram (23 lb) wheeled robotic rover named Sojourner, which was the first rover to operate on the surface of Mars. In addition to scientific objectives, the Mars Pathfinder mission was also a "proof-of-concept" for various technologies, such as an airbag landing system and automated obstacle avoidance, both later exploited by the Mars Exploration Rovers.
Mars Global Surveyor

After the 1992 failure of NASA's Mars Observer orbiter, NASA retooled and launched Mars Global Surveyor (MGS). Mars Global Surveyor launched on November 7, 1996, and entered orbit on September 12, 1997. After a year and a half trimming its orbit from a looping ellipse to a circular track around the planet, the spacecraft began its primary mapping mission in March 1999. It observed the planet from a low-altitude, nearly polar orbit over the course of one complete Martian year, the equivalent of nearly two Earth years. Mars Global Surveyor completed its primary mission on January 31, 2001, and completed several extended mission phases until communication was lost in 2007.
The mission studied the entire Martian surface, atmosphere, and interior, and returned more data about the red planet than all previous Mars missions combined. The data has been archived and remains available publicly.

Among key scientific findings, Global Surveyor took pictures of gullies and debris flow features that suggest there may be current sources of liquid water, similar to an aquifer, at or near the surface of the planet. Similar channels on Earth are formed by flowing water, but on Mars the temperature is normally too cold and the atmosphere too thin to sustain liquid water. Nevertheless, many scientists hypothesize that liquid groundwater can sometimes surface on Mars, erode gullies and channels, and pool at the bottom before freezing and evaporating.
Magnetometer readings showed that the planet's magnetic field is not globally generated in the planet's core, but is localized in particular areas of the crust. New temperature data and closeup images of the Martian moon Phobos showed that its surface is composed of powdery material at least 1 metre (3 feet) thick, caused by millions of years of meteoroid impacts. Data from the spacecraft's laser altimeter gave scientists their first 3-D views of Mars' north polar ice cap in January 1999.
Faulty software uploaded to the vehicle in June 2006 caused the spacecraft to orient its solar panels incorrectly several months later, resulting in battery overheating and subsequent failure. On November 5, 2006, MGS lost contact with Earth. NASA ended efforts to restore communication on January 28, 2007.
Mars Odyssey and Mars Express

2001 Mars Odyssey · Mars

Mars Express · Mars
In 2001, NASA's Mars Odyssey orbiter arrived at Mars. Its mission is to use spectrometers and imagers to hunt for evidence of past or present water and volcanic activity on Mars. In 2002, it was announced that the probe's gamma-ray spectrometer and neutron spectrometer had detected large amounts of hydrogen, indicating that there are vast deposits of water ice in the upper three meters of Mars' soil within 60° latitude of the south pole.
On June 2, 2003, the European Space Agency's Mars Express set off from Baikonur Cosmodrome to Mars. The Mars Express craft consists of the Mars Express Orbiter and the stationary lander Beagle 2. The lander carried a digging device and the smallest mass spectrometer created to date, as well as a range of other devices, on a robotic arm in order to accurately analyze soil beneath the dusty surface to look for biosignatures and biomolecules.
The orbiter entered Mars orbit on December 25, 2003, and Beagle 2 entered Mars' atmosphere the same day. However, attempts to contact the lander failed. Communications attempts continued throughout January, but Beagle 2 was declared lost in mid-February, and a joint inquiry was launched by the UK and ESA. The Mars Express Orbiter confirmed the presence of water ice and carbon dioxide ice at the planet's south pole, while NASA had previously confirmed their presence at the north pole of Mars.
The lander's fate remained a mystery until it was located intact on the surface of Mars in a series of images from the Mars Reconnaissance Orbiter. The images suggest that two of the spacecraft's four solar panels failed to deploy, blocking the spacecraft's communications antenna. Beagle 2 is the first British and first European probe to achieve a soft landing on Mars.
MER, Opportunity rover, Spirit rover, Phoenix lander

NASA's Mars Exploration Rover Mission (MER), started in 2003, was a robotic space mission involving two rovers, Spirit (MER-A) and Opportunity, (MER-B) that explored the Martian surface geology. The mission's scientific objective was to search for and characterize a wide range of rocks and soils that hold clues to past water activity on Mars. The mission was part of NASA's Mars Exploration Program, which includes three previous successful landers: the two Viking program landers in 1976; and Mars Pathfinder probe in 1997.
Mars Reconnaissance Orbiter

The Mars Reconnaissance Orbiter (MRO) is a multipurpose spacecraft designed to conduct reconnaissance and exploration of Mars from orbit. The US$720 million spacecraft was built by Lockheed Martin under the supervision of the Jet Propulsion Laboratory, launched August 12, 2005, and entered Mars orbit on March 10, 2006.
The MRO contains a host of scientific instruments such as the HiRISE camera, CTX camera, CRISM, and SHARAD. The HiRISE camera is used to analyze Martian landforms, whereas CRISM and SHARAD can detect water, ice, and minerals on and below the surface. Additionally, MRO is paving the way for upcoming generations of spacecraft through daily monitoring of Martian weather and surface conditions, searching for future landing sites, and testing a new telecommunications system that enable it to send and receive information at an unprecedented bitrate, compared to previous Mars spacecraft. Data transfer to and from the spacecraft occurs faster than all previous interplanetary missions combined and allows it to serve as an important relay satellite for other missions.
Rosetta and Dawn swingbys
The ESA Rosetta space probe mission to the comet 67P/Churyumov-Gerasimenko flew within 250 km of Mars on February 25, 2007, in a gravitational slingshot designed to slow and redirect the spacecraft.
The NASA Dawn spacecraft used the gravity of Mars in 2009 to change direction and velocity on its way to Vesta, and tested out Dawn's cameras and other instruments on Mars.
Fobos-Grunt
On November 8, 2011, Russia's Roscosmos launched an ambitious mission called Fobos-Grunt. It consisted of a lander aimed to retrieve a sample back to Earth from Mars' moon Phobos, and place the Chinese Yinghuo-1 probe in Mars' orbit. The Fobos-Grunt mission suffered a complete control and communications failure shortly after launch and was left stranded in low Earth orbit, later falling back to Earth. The Yinghuo-1 satellite and Fobos-Grunt underwent destructive re-entry on January 15, 2012, finally disintegrating over the Pacific Ocean.
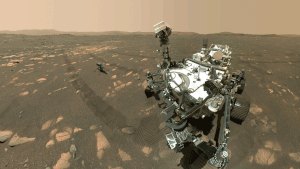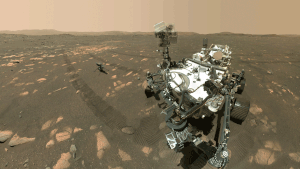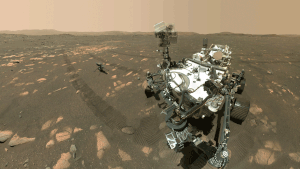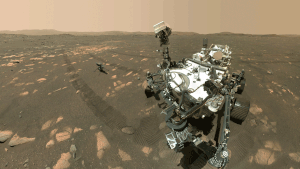
Curiosity rover

The NASA Mars Science Laboratory mission with its rover named Curiosity, was launched on November 26, 2011, and landed on Mars on August 6, 2012, on Aeolis Palus in Gale Crater. The rover carries instruments designed to look for past or present conditions relevant to the past or present habitability of Mars.
MAVEN
NASA's MAVEN is an orbiter mission to study the upper atmosphere of Mars. It will also serve as a communications relay satellite for robotic landers and rovers on the surface of Mars. MAVEN was launched 18 November 2013 and reached Mars on 22 September 2014.
Mars Orbiter Mission
The Mars Orbiter Mission, also called Mangalyaan, was launched on 5 November 2013 by the Indian Space Research Organisation (ISRO). It was successfully inserted into Martian orbit on 24 September 2014. The mission is a technology demonstrator, and as secondary objective, it will also study the Martian atmosphere. This is India's first mission to Mars, and with it, ISRO became the fourth space agency to successfully reach Mars after the Soviet Union, NASA (USA) and ESA (Europe). It was completed in a record low budget of $71 million, making it the least-expensive Mars mission to date. The mission concluded on September 27, 2022, after contact was lost.
Trace Gas Orbiter and EDM
The ExoMars Trace Gas Orbiter
is an atmospheric research orbiter built in collaboration between ESA
and Roscosmos. It was injected into Mars orbit on 19 October 2016 to
gain a better understanding of methane (CH
4)
and other trace gases present in the Martian atmosphere that could be
evidence for possible biological or geological activity. The
Schiaparelli EDM lander was destroyed when trying to land on the surface
of Mars.
InSight and MarCO

(Perseverance rover; Ingenuity Mars helicopter; InSight lander; Odyssey orbiter; MAVEN orbiter; Curiosity rover; Mars Reconnaissance Orbiter)
In August 2012, NASA selected InSight, a $425 million lander mission with a heat flow probe and seismometer, to determine the deep interior structure of Mars. InSight landed successfully on Mars on 26 November 2018. Valuable data on the atmosphere, surface and the planet's interior were gathered by Insight. Insight's mission was declared as ended on 21 December 2022.
Two flyby CubeSats called MarCO were launched with InSight on 5 May 2018 to provide real-time telemetry during the entry and landing of InSight. The CubeSats separated from the Atlas V booster 1.5 hours after launch and traveled their own trajectories to Mars.
Hope
The United Arab Emirates launched the Hope Mars Mission, in July 2020 on the Japanese H-IIA booster. It was successfully placed into orbit on 9 February 2021. It is studying the Martian atmosphere and weather.
Tianwen-1 and Zhurong rover
Tianwen-1 was a Chinese mission launched on 23 July 2020 which included an orbiter, a lander, and a 240-kilogram (530 lb) rover along with a package of deployable and remote cameras. Tianwen-1 entered orbit on 10 February 2021 and the Zhurong rover successfully landed on 14 May 2021 and deployed on 22 May 2021. As of May 2022, Zhurong had been in operation for 347 Martian days and had traveled 1,921 meters across Mars.
Mars 2020, Perseverance rover, Ingenuity helicopter
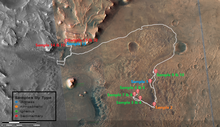
The Mars 2020 mission by NASA was launched on 30 July 2020 on a United Launch Alliance Atlas V rocket from Cape Canaveral. It is based on the Mars Science Laboratory design. The scientific payload is focused on astrobiology. It includes the Perseverance rover and the Ingenuity helicopter. Unlike older rovers that relied on solar power, Perseverance is nuclear powered, to survive longer than its predecessors in this harsh, dusty environment. The car-size rover weighs about 1 ton, with a robotic arm that reaches about 7 feet (2.1 m), zoom cameras, a chemical analyzer and a rock drill.
After traveling 293 million miles (471 million km) to reach Mars over the course of more than six months, Perseverance successfully landed on February 18, 2021. Its initial mission is set for at least one Martian year, or 687 Earth days. It will search for signs of ancient life and explore the red planet's surface.
As of October 19, 2021, Perseverance had captured the first sounds from Mars. Recordings consisted of five hours of Martian wind gusts, rover wheels crunching over gravel, and motors whirring as the spacecraft moves its arm. The sounds give researchers clues about the atmosphere, such as how far sound travels on the planet.
Future missions
- As part of the ExoMars program, ESA and the Roscosmos planned to send the Rosalind Franklin rover in 2022 to search for evidence of past or present microscopic life on Mars. The lander that was planned to deliver the rover is called Kazachok, and it would have performed scientific studies for about 2 years. This mission has been delayed indefinitely as a result of the 2022 Russian invasion of Ukraine.
- EscaPADE (Escape and Plasma Acceleration and Dynamics Explorers) by the University of California, Berkeley, is a planned twin-spacecraft NASA Mars orbiter mission to study the structure, composition, variability and dynamics of Mars' magnetosphere and atmospheric escape processes. The EscaPADE orbiters were originally to be launched in 2022 as secondary payloads on a Falcon Heavy together with the Psyche and Janus missions, but will now be remanifested on different flight, yet to be determined.
- India's ISRO plans to send a follow-up mission to its Mars Orbiter Mission in 2024; it is called Mars Orbiter Mission 2 (MOM-2) and it will consist of an orbiter.
Proposals
- The Finnish-Russian Mars MetNet concept would use multiple small meteorological stations on Mars to establish a widespread observation network to investigate the planet's atmospheric structure, physics and meteorology. The MetNet precursor or demonstrator was considered for a piggyback launch on Fobos-Grunt, and on the two proposed to fly on the 2016 and 2020 ExoMars spacecraft.
- Tianwen-3 is a Chinese mission to return samples of Martian soil to Earth. The mission would launch in late 2028, with a lander and ascent vehicle and an orbiter and return module launched separately on two rockets. The samples would be returned to Earth by July 2031.
- NASA-ESA Mars Sample Return is a three-launch architecture concept for a sample return mission, which uses a rover to cache small samples, a Mars ascent stage to send it into orbit, and an orbiter to rendezvous with it above Mars and take it to Earth. Solar-electric propulsion could allow a one launch sample return instead of three.
- The Mars-Grunt is a Russian mission concept to bring a sample of Martian soil to Earth.
- The Mars Scout Program's SCIM would involve a probe grazing the upper atmosphere of Mars to collect dust and air for return to Earth.
- JAXA is working on a mission concept called MELOS rover that would look for biosignatures of extant life on Mars.
- Indian Space Research Organisation has proposed a Mangalyaan-3 mission that will include a lander and rover on Mars.
Other future mission concepts include polar probes, Martian aircraft and a network of small meteorological stations. Longterm areas of study may include Martian lava tubes, resource utilization, and electronic charge carriers in rocks. Micromissions are another possibility, such as piggybacking a small spacecraft on an Ariane 5 rocket and using a lunar gravity assist to get to Mars.
Human mission proposals

The human exploration of Mars has been an aspiration since the earliest days of modern rocketry; Robert H. Goddard credits the idea of reaching Mars as his own inspiration to study the physics and engineering of space flight. Proposals for human exploration of Mars have been made throughout the history of space exploration; currently there are multiple active plans and programs to put humans on Mars within the next ten to thirty years, both governmental and private, some of which are listed below.
NASA

Human exploration by the United States was identified as a long-term goal in the Vision for Space Exploration announced in 2004 by then US President George W. Bush. The planned Orion spacecraft would be used to send a human expedition to Earth's moon by 2020 as a stepping stone to a Mars expedition. On September 28, 2007, NASA administrator Michael D. Griffin stated that NASA aims to put a person on Mars by 2037.
On December 2, 2014, NASA's Advanced Human Exploration Systems and Operations Mission Director Jason Crusan and Deputy Associate Administrator for Programs James Reuthner announced tentative support for the Boeing "Affordable Mars Mission Design" including radiation shielding, centrifugal artificial gravity, in-transit consumable resupply, and a lander which can return. Reuthner suggested that if adequate funding was forthcoming, the proposed mission would be expected in the early 2030s.
On October 8, 2015, NASA published its official plan for human exploration and colonization of Mars. They called it "Journey to Mars". The plan operates through three distinct phases leading up to fully sustained colonization.
- The first stage, already underway, is the "Earth Reliant" phase. This phase continues utilizing the International Space Station until 2024; validating deep space technologies and studying the effects of long-duration space missions on the human body.
- The second stage, "Proving Ground," moves away from Earth reliance and ventures into cislunar space for most of its tasks. This is when NASA plans to capture an asteroid, test deep space habitation facilities, and validate the capabilities required for human exploration of Mars. Finally, phase three is the transition to independence from Earth resources.
- The last stage, the "Earth Independent" phase, includes long-term missions on the lunar surface which leverage surface habitats that only require routine maintenance, and the harvesting of Martian resources for fuel, water, and building materials. NASA is still aiming for human missions to Mars in the 2030s, though Earth independence could take decades longer.
On August 28, 2015, NASA funded a year-long simulation to study the effects of a year-long Mars mission on six scientists. The scientists lived in a biodome on a Mauna Loa mountain in Hawaii with limited connection to the outside world and were only allowed outside if they were wearing spacesuits.
NASA's human Mars exploration plans have evolved through the NASA Mars Design Reference Missions, a series of design studies for human exploration of Mars.
In 2017, the focus of NASA shifted to a return to the Moon by 2024 with the Artemis program, a flight to Mars could follow after this project.
SpaceX
The long-term goal of the private corporation SpaceX is the establishment of routine flights to Mars to enable colonization. To this end, the company is developing Starship, a spacecraft capable of crew transportation to Mars and other celestial bodies, along with its booster Super Heavy. In 2017 SpaceX announced plans to send two uncrewed Starships to Mars by 2022, followed by two more uncrewed flights and two crewed flights in 2024. Starship is planned to have a payload of at least 100 tonnes. Starship is designed to use a combination of aerobraking and propulsive descent, utilizing fuel produced from a Mars (in situ resource utilization) facility. As of mid 2021, the Starship development program has seen successful testing of several Starship prototypes.
Zubrin
Mars Direct, a low-cost human mission proposed by Robert Zubrin, founder of the Mars Society, would use heavy-lift Saturn V class rockets, such as the Ares V, to skip orbital construction, LEO rendezvous, and lunar fuel depots. A modified proposal, called "Mars to Stay", involves not returning the first immigrant explorers immediately, if ever (see Colonization of Mars).
Probing difficulties

| Spacecraft | Outcome |
|---|---|
| Phobos 1 | Failure |
| Phobos 2 | Partial success |
| Mars Observer | Failure |
| Mars 96 | Failure |
| Mars Pathfinder | Success |
| Mars Global Surveyor | Success |
| Mars Climate Orbiter | Failure |
| Mars Polar Lander | Failure |
| Deep Space 2 | Failure |
| Nozomi | Failure |
The challenge, complexity and length of Mars missions have led to many mission failures. The high failure rate of missions attempting to explore Mars is informally called the "Mars Curse" or "Martian Curse". The phrase "Galactic Ghoul" or "Great Galactic Ghoul" refers to a fictitious space monster that subsists on a diet of Mars probes, and is sometimes facetiously used to "explain" the recurring difficulties.
Two Soviet probes were sent to Mars in 1988 as part of the Phobos program. Phobos 1 operated normally until an expected communications session on 2 September 1988 failed to occur. The problem was traced to a software error, which deactivated Phobos 1's attitude thrusters, causing the spacecraft's solar arrays to no longer point at the Sun, depleting Phobos 1's batteries. Phobos 2 operated normally throughout its cruise and Mars orbital insertion phases on January 29, 1989, gathering data on the Sun, interplanetary medium, Mars, and Phobos. Shortly before the final phase of the mission – during which the spacecraft was to approach within 50 m of Phobos' surface and release two landers, one a mobile 'hopper', the other a stationary platform – contact with Phobos 2 was lost. The mission ended when the spacecraft signal failed to be successfully reacquired on March 27, 1989. The cause of the failure was determined to be a malfunction of the on-board computer.
Just a few years later in 1992 Mars Observer, launched by NASA, failed as it approached Mars. Mars 96, an orbiter launched on November 16, 1996, by Russia failed, when the planned second burn of the Block D-2 fourth stage did not occur.
Following the success of Global Surveyor and Pathfinder, another spate of failures occurred in 1998 and 1999, with the Japanese Nozomi orbiter and NASA's Mars Climate Orbiter, Mars Polar Lander, and Deep Space 2 penetrators all suffering various fatal errors. The Mars Climate Orbiter was noted for mixing up U.S. customary units with metric units, causing the orbiter to burn up while entering Mars' atmosphere.
The European Space Agency has also attempted to land two probes on the Martian surface; Beagle 2, a British-built lander that failed to deploy its solar arrays properly after touchdown in December 2003, and Schiaparelli, which was flown along the ExoMars Trace Gas Orbiter. Contact with the Schiaparelli EDM lander was lost 50 seconds before touchdown. It was later confirmed that the lander struck the surface at a high velocity, possibly exploding.





















