| Substantia nigra | |
|---|---|
 Substantia nigra highlighted in red. | |
 Section through superior colliculus showing Substantia nigra. | |
| Details | |
| Part of | Midbrain, Basal ganglia |
| Identifiers | |
| Latin | Substantia nigra |
| Acronym(s) | SN |
| MeSH | D013378 |
| NeuroNames | 536 |
| NeuroLex ID | birnlex_789 |
| TA98 | A14.1.06.111 |
| TA2 | 5881 |
| FMA | 67947 |
The substantia nigra (SN) is a basal ganglia structure located in the midbrain that plays an important role in reward and movement. Substantia nigra is Latin for "black substance", reflecting the fact that parts of the substantia nigra appear darker than neighboring areas due to high levels of neuromelanin in dopaminergic neurons. Parkinson's disease is characterized by the loss of dopaminergic neurons in the substantia nigra pars compacta.
Although the substantia nigra appears as a continuous band in brain sections, anatomical studies have found that it actually consists of two parts with very different connections and functions: the pars compacta (SNpc) and the pars reticulata (SNpr). The pars compacta serves mainly as a projection to the basal ganglia circuit, supplying the striatum with dopamine. The pars reticulata conveys signals from the basal ganglia to numerous other brain structures.
Structure


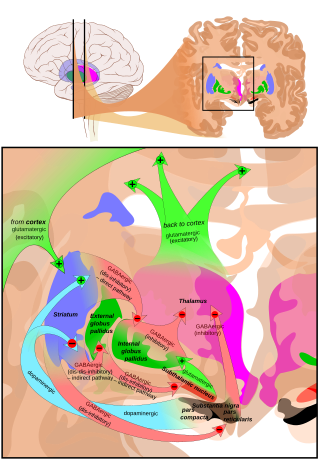
The substantia nigra, along with four other nuclei, is part of the basal ganglia. It is the largest nucleus in the midbrain, lying dorsal to the cerebral peduncles. Humans have two substantiae nigrae, one on each side of the midline.
The SN is divided into two parts: the pars reticulata (SNpr) and the pars compacta (SNpc), which lies medial to the pars reticulata. Sometimes, a third region, the pars lateralis, is mentioned, though it is usually classified as part of the pars reticulata. The (SNpr) and the internal globus pallidus (GPi) are separated by the internal capsule.
Pars reticulata
The pars reticulata bears a strong structural and functional resemblance to the internal part of the globus pallidus. The two are sometimes considered parts of the same structure, separated by the white matter of the internal capsule. Like those of the globus pallidus, the neurons in pars reticulata are mainly GABAergic.
Afferent connections
The main input to the SNpr derives from the striatum. It comes by two routes, known as the direct and indirect pathways. The direct pathway consists of axons from medium spiny cells in the striatum that project directly to pars reticulata. The indirect pathway consists of three links: a projection from striatal medium spiny cells to the external part of the globus pallidus; a GABAergic projection from the globus pallidus to the subthalamic nucleus, and a glutamatergic projection from the subthalamic nucleus to the pars reticulata. Thus, striatal activity via the direct pathway exerts an inhibitory effect on neurons in the (SNpr) but an excitatory effect via the indirect pathway. The direct and indirect pathways originate from different subsets of striatal medium spiny cells: They are tightly intermingled, but express different types of dopamine receptors, as well as showing other neurochemical differences.
Efferent connections
Significant projections occur to the thalamus (ventral lateral and ventral anterior nuclei), superior colliculus, and other caudal nuclei from the pars reticulata (the nigrothalamic pathway), which use GABA as their neurotransmitter. In addition, these neurons form up to five collaterals that branch within both the pars compacta and pars reticulata, likely modulating dopaminergic activity in the pars compacta.
Function
The substantia nigra is an important player in brain function, in particular, in eye movement, motor planning, reward-seeking, learning, and addiction. Many of the substantia nigra's effects are mediated through the striatum. The nigral dopaminergic input to the striatum via the nigrostriatal pathway is intimately linked with the striatum's function. The co-dependence between the striatum and substantia nigra can be seen in this way: when the substantia nigra is electrically stimulated, no movement occurs; however, the symptoms of nigral degeneration due to Parkinson's is a poignant example of the substantia nigra's influence on movement. In addition to striatum-mediated functions, the substantia nigra also serves as a major source of GABAergic inhibition to various brain targets.
Pars reticulata
The pars reticulata of the substantia nigra is an important processing center in the basal ganglia. The GABAergic neurons in the pars reticulata convey the final processed signals of the basal ganglia to the thalamus and superior colliculus. In addition, the pars reticulata also inhibits dopaminergic activity in the pars compacta via axon collaterals, although the functional organization of these connections remains unclear.
The GABAergic neurons of the pars reticulata spontaneously fire action potentials. In rats, the frequency of action potentials is roughly 25 Hz. The purpose of these spontaneous action potentials is to inhibit targets of the basal ganglia, and decreases in inhibition are associated with movement. The subthalamic nucleus gives excitatory input that modulates the rate of firing of these spontaneous action potentials. However, lesion of the subthalamic nucleus leads to only a 20% decrease in pars reticulata firing rate, suggesting that the generation of action potentials in the pars reticulata is largely autonomous, as exemplified by the pars reticulata's role in saccadic eye movement. A group of GABAergic neurons from the pars reticulata projects to the superior colliculus, exhibiting a high level of sustained inhibitory activity. Projections from the caudate nucleus to the superior colliculus also modulate saccadic eye movement. Altered patterns of pars reticulata firing such as single-spike or burst firing are found in Parkinson's disease and epilepsy.
Pars compacta
The most prominent function of the pars compacta is motor control, though the substantia nigra's role in motor control is indirect; electrical stimulation of the substantia nigra does not result in movement, due to mediation of the striatum in the nigral influence of movement. The pars compacta sends excitatory input to the striatum via D1 pathway that excites and activates the striatum, resulting in the release of GABA onto the globus pallidus to inhibit its inhibitory effects on the thalamic nucleus. This causes the thalamocortical pathways to become excited and transmits motor neuron signals to the cerebral cortex to allow the initiation of movement, which is absent in Parkinson's disease. However, lack of pars compacta neurons has a large influence on movement, as evidenced by the symptoms of Parkinson's. The motor role of the pars compacta may involve fine motor control, as has been confirmed in animal models with lesions in that region.
The pars compacta is heavily involved in learned responses to stimuli. In primates, dopaminergic neuron activity increases in the nigrostriatal pathway when a new stimulus is presented. Dopaminergic activity decreases with repeated stimulus presentation. However, behaviorally significant stimulus presentation (i.e. rewards) continues to activate dopaminergic neurons in the substantia nigra pars compacta. Dopaminergic projections from the ventral tegmental area (bottom part of the "midbrain" or mesencephalon) to the prefrontal cortex (mesocortical pathway) and to the nucleus accumbens (mesolimbic pathway – "meso" referring to "from the mesencephalon"... specifically the ventral tegmental area) are implicated in reward, pleasure, and addictive behavior. The pars compacta is also important in spatial learning, the observations about one's environment and location in space. Lesions in the pars compacta lead to learning deficits in repeating identical movements, and some studies point to its involvement in a dorsal striatal-dependent, response-based memory system that functions relatively independent of the hippocampus, which is traditionally believed to subserve spatial or episodic-like memory functions.
The pars compacta also plays a role in temporal processing and is activated during time reproduction. Lesions in the pars compacta leads to temporal deficits. As of late, the pars compacta has been suspected of regulating the sleep-wake cycle, which is consistent with symptoms such as insomnia and REM sleep disturbances that are reported by patients with Parkinson's disease. Even so, partial dopamine deficits that do not affect motor control can lead to disturbances in the sleep-wake cycle, especially REM-like patterns of neural activity while awake, especially in the hippocampus.
Clinical significance
The substantia nigra is critical in the development of many diseases and syndromes, including parkinsonism and Parkinson's disease. There exist a study showing that high-frequency stimulation delivery to the left substantia nigra can induce transient acute depression symptoms.
Parkinson's disease

Parkinson's disease is a neurodegenerative disease characterized, in part, by the death of dopaminergic neurons in the SNpc. The major symptoms of Parkinson's disease include tremor, akinesia, bradykinesia, and stiffness. Other symptoms include disturbances to posture, fatigue, sleep abnormalities, and depressed mood.
The cause of death of dopaminergic neurons in the SNpc is unknown. However, some contributions to the unique susceptibility of dopaminergic neurons in the pars compacta have been identified. For one, dopaminergic neurons show abnormalities in mitochondrial complex 1, causing aggregation of alpha-synuclein; this can result in abnormal protein handling and neuron death. Secondly, dopaminergic neurons in the pars compacta contain less calbindin than other dopaminergic neurons. Calbindin is a protein involved in calcium ion transport within cells, and excess calcium in cells is toxic. The calbindin theory would explain the high cytotoxicity of Parkinson's in the substantia nigra compared to the ventral tegmental area. Regardless of the cause of neuronal death, the plasticity of the pars compacta is very robust; Parkinsonian symptoms do not generally appear until at least 30% of pars compacta dopaminergic neurons have died. Most of this plasticity occurs at the neurochemical level; dopamine transport systems are slowed, allowing dopamine to linger for longer periods of time in the chemical synapses in the striatum.
Menke, Jbabdi, Miller, Matthews and Zari (2010) used diffusion tensor imaging, as well as T1 mapping to assess volumetric differences in the SNpc and SNpr, in participants with Parkinson's compared to healthy individuals. These researchers found that participants with Parkinson's consistently had a smaller substantia nigra, specifically in the SNpr. Because the SNpr is connected to the posterior thalamus, ventral thalamus and specifically, the motor cortex, and because participants with Parkinson's disease report having a smaller SNprs (Menke, Jbabdi, Miller, Matthews and Zari, 2010), the small volume of this region may be responsible for motor impairments found in Parkinson's disease patients. This small volume may be responsible for weaker and/or less controlled motor movements, which may result in the tremors often experienced by those with Parkinson's.
Oxidative stress and oxidative damage in the SNpc are likely key drivers in the etiology of Parkinson’s disease as individuals age. DNA damages caused by oxidative stress can be repaired by processes modulated by alpha-synuclein. Alpha synuclein is expressed in the substantia nigra, but its DNA repair function appears to be compromised in Lewy body inclusion bearing neurons. This loss may trigger cell death.
Schizophrenia
Increased levels of dopamine have long been implicated in the development of schizophrenia. However, much debate continues to this day surrounding this dopamine hypothesis of schizophrenia. Despite the controversy, dopamine antagonists remain a standard and successful treatment for schizophrenia. These antagonists include first generation (typical) antipsychotics such as butyrophenones, phenothiazines, and thioxanthenes. These drugs have largely been replaced by second-generation (atypical) antipsychotics such as clozapine and paliperidone. In general, these drugs do not act on dopamine-producing neurons themselves, but on the receptors on the post-synaptic neuron.
Other, non-pharmacological evidence in support of the dopamine hypothesis relating to the substantia nigra include structural changes in the pars compacta, such as reduction in synaptic terminal size. Other changes in the substantia nigra include increased expression of NMDA receptors in the substantia nigra, and reduced dysbindin expression. Increased NMDA receptors may point to the involvement of glutamate-dopamine interactions in schizophrenia. Dysbindin, which has been (controversially) linked to schizophrenia, may regulate dopamine release, and low expression of dysbindin in the substantia nigra may be important in schizophrenia etiology. Due to the changes to the substantia nigra in the schizophrenic brain, it may eventually be possible to use specific imaging techniques (such as neuromelanin-specific imaging) to detect physiological signs of schizophrenia in the substantia nigra.
Wooden Chest Syndrome
Wooden chest, also called fentanyl chest wall rigidity syndrome, is a rare side effect of synthetic opioids such as Fentanyl, Sulfentanil, Alfentanil, Remifentanil. It results in a generalised increase in skeletal muscle tone. The mechanism is thought to be via increased dopamine release and decreased GABA release in the nerves of the substantia nigra/striatum. The effect is most pronounced on the chest wall muscles and can lead to impaired ventilation. The condition is most commonly observed in anaesthesia where rapid and high doses of these drugs are given intravenously.
Multiple system atrophy
Multiple system atrophy characterized by neuronal degeneration in the striatum and substantia nigra was previously called striatonigral degeneration.
Chemical modification of the substantia nigra
Chemical manipulation and modification of the substantia nigra is important in the fields of neuropharmacology and toxicology. Various compounds such as levodopa and MPTP are used in the treatment and study of Parkinson's disease, and many other drugs have effects on the substantia nigra.
Amphetamine and trace amines
Studies have shown that, in certain brain regions, amphetamine and trace amines increase the concentrations of dopamine in the synaptic cleft, thereby heightening the response of the post-synaptic neuron. The various mechanisms by which amphetamine and trace amines affect dopamine concentrations have been studied extensively, and are known to involve both DAT and VMAT2. Amphetamine is similar in structure to dopamine and trace amines; as a consequence, it can enter the presynaptic neuron via DAT as well as by diffusing through the neural membrane directly. Upon entering the presynaptic neuron, amphetamine and trace amines activate TAAR1, which, through protein kinase signaling, induces dopamine efflux, phosphorylation-dependent DAT internalization, and non-competitive reuptake inhibition. Because of the similarity between amphetamine and trace amines, it is also a substrate for monoamine transporters; as a consequence, it (competitively) inhibits the reuptake of dopamine and other monoamines by competing with them for uptake, as well.
In addition, amphetamine and trace amines are substrates for the neuronal vesicular monoamine transporter, vesicular monoamine transporter 2 (VMAT2). When amphetamine is taken up by VMAT2, the vesicle releases (effluxes) dopamine molecules into the cytosol in exchange.
Cocaine
Cocaine's mechanism of action in the human brain includes the inhibition of dopamine reuptake, which accounts for cocaine's addictive properties, as dopamine is the critical neurotransmitter for reward. However, cocaine is more active in the dopaminergic neurons of the ventral tegmental area than the substantia nigra. Cocaine administration increases metabolism in the substantia nigra, which can explain the altered motor function seen in cocaine-using subjects. The inhibition of dopamine reuptake by cocaine also inhibits the firing of spontaneous action potentials by the pars compacta. The mechanism by which cocaine inhibits dopamine reuptake involves its binding to the dopamine transporter protein. However, studies show that cocaine can also cause a decrease in DAT mRNA levels, most likely due to cocaine blocking dopamine receptors rather than direct interference with transcriptional or translational pathways.
Inactivation of the substantia nigra could prove to be a possible treatment for cocaine addiction. In a study of cocaine-dependent rats, inactivation of the substantia nigra via implanted cannulae greatly reduced cocaine addiction relapse.
Levodopa
The substantia nigra is the target of chemical therapeutics for the treatment of Parkinson's disease. Levodopa (commonly referred to as L-DOPA), the dopamine precursor, is the most commonly prescribed medication for Parkinson's disease, despite controversy concerning the neurotoxicity of dopamine and L-DOPA. The drug is especially effective in treating patients in the early stages of Parkinson's, although it does lose its efficacy over time. Levodopa can cross the blood–brain barrier and increases dopamine levels in the substantia nigra, thus alleviating the symptoms of Parkinson's disease. The drawback of levodopa treatment is that it treats the symptoms of Parkinson's (low dopamine levels), rather than the cause (the death of dopaminergic neurons in the substantia nigra).
MPTP
MPTP, is a neurotoxin specific to dopaminergic cells in the brain, specifically in the substantia nigra. MPTP was brought to the spotlight in 1982 when heroin users in California displayed Parkinson's-like symptoms after using MPPP contaminated with MPTP. The patients, who were rigid and almost completely immobile, responded to levodopa treatment. No remission of the Parkinson's-like symptoms was reported, suggesting irreversible death of the dopaminergic neurons. The proposed mechanism of MPTP involves disruption of mitochondrial function, including disruption of metabolism and creation of free radicals.
Soon after, MPTP was tested in animal models for its efficacy in inducing Parkinson's disease (with success). MPTP induced akinesia, rigidity, and tremor in primates, and its neurotoxicity was found to be very specific to the substantia nigra pars compacta. In other animals, such as rodents, the induction of Parkinson's by MPTP is incomplete or requires much higher and frequent doses than in primates. Today, MPTP remains the most favored method to induce Parkinson's disease in animal models.