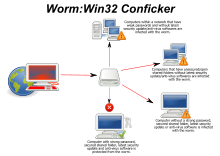
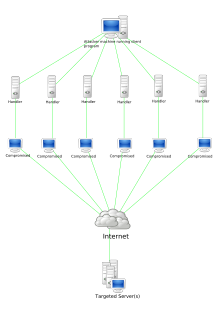
Internet manipulation refers to the co-optation of digital technology, such as social media algorithms and automated scripts, for commercial, social or political purposes. Such tactics may be employed with the explicit intent to manipulate public opinion, polarise citizens, silence political dissidents, harm corporate or political adversaries, and improve personal or brand reputation. Hackers, hired professionals and private citizens have all been reported to engage in internet manipulation using software – typically Internet bots such as social bots, votebots and clickbots.
Cognitive hacking refers to a cyberattack that aims to change users' perceptions and corresponding behaviors.
Internet manipulation is sometimes also used to describe selective Internet censorship or violations of net neutrality.
Issues
- Behavior Manipulation: Fake news, disinformation, and AI can secretly affect behavior. This is a different issue from affecting cognitive beliefs, as this can operate outside of awareness, making it harder to detect.
- High-arousal emotion virality: It has been found that content that evokes high-arousal emotions (e.g. awe, anger, anxiety or with hidden sexual meaning) is more viral and that content that holds one or many of these elements: surprising, interesting, or useful is taken into consideration.
- Simplicity over complexity: Providing and perpetuating simple explanations for complex circumstances may be used for online manipulation. Often such are easier to believe, come in advance of any adequate investigations and have a higher virality than any complex, nuanced explanations and information.
- Peer-influence: Prior collective ratings of an web content influences ones own perception of it. In 2015 it was shown that the perceived beauty of a piece of artwork in an online context varies with external influence as confederate ratings were manipulated by opinion and credibility for participants of an experiment who were asked to evaluate a piece of artwork. Furthermore, on Reddit, it has been found that content that initially gets a few down- or upvotes often continues going negative, or vice versa. This is referred to as "bandwagon/snowball voting" by reddit users and administrators.
- Filter bubbles: Echo chambers and filter bubbles might be created by Website administrators or moderators locking out people with altering viewpoints or by establishing certain rules or by the typical member viewpoints of online sub/communities or Internet "tribes"
- Confirmation bias & manipulated prevalence: Fake news does not need to be read but has an effect in quantity and emotional effect by its headlines and sound bites alone. Specific points, views, issues and people's apparent prevalence can be amplified, stimulated or simulated. (See also: Mere-exposure effect)
- Information timeliness and uncorrectability: Clarifications, conspiracy busting and fake news exposure often come late when the damage is already done and/or do not reach the bulk of the audience of the associated misinformation
- Psychological targeting: Social media activities and other data can be used to analyze the personality of people and predict their behaviour and preferences. Dr Michal Kosinski developed such a procedure. Such can be used for media or information tailored to a person's psyche e.g. via Facebook. According to reports such may have played an integral part in Donald Trump's win.
Algorithms, echo chambers and polarization
Due to overabundance of online content, social networking platforms and search engines have leveraged algorithms to tailor and personalize users' feeds based on their individual preferences. However, algorithms also restrict exposure to different viewpoints and content. This is commonly referred to as "echo-chambers" and "filter-bubbles".
With the help of algorithms, filter bubbles influence users' choices and perception of reality by giving the impression that a particular point of view or representation is widely shared. Following the 2016 referendum of membership of the European Union in the United Kingdom and the United States presidential elections, this gained attention as many individuals confessed their surprise at results that seemed very distant from their expectations. The range of pluralism is influenced by the personalized individualization of the services and the way it diminishes choice. Five manipulative verbal influences were found in media texts. There are self-expression, semantic speech strategies, persuasive strategies, swipe films and information manipulation. The vocabulary toolkit for speech manipulation includes euphemism, mood vocabulary, situational adjectives, slogans, verbal metaphors, etc.
Research on echo chambers from Flaxman, Goel, and Rao, Pariser, and Grömping suggest that use of social media and search engines tends to increase ideological distance among individuals.
Comparisons between online and off-line segregation have indicated how segregation tends to be higher in face-to-face interactions with neighbors, co-workers, or family members, and reviews of existing research have indicated how available empirical evidence does not support the most pessimistic views about polarization. A study conducted by Bakshy, Messing, and Adamic from Facebook and the University of Michigan, for example, has suggested that individuals’ own choices drive algorithmic filtering, limiting exposure to a range of content. While algorithms may not be causing polarization, they could amplify it, representing a significant component of the new information landscape.
Research and use by intelligence and military agencies
The Joint Threat Research Intelligence Group unit of the Government Communications Headquarters (GCHQ), the British intelligence agency was revealed as part of the global surveillance disclosures in documents leaked by the former National Security Agency contractor Edward Snowden and its mission scope includes using "dirty tricks" to "destroy, deny, degrade [and] disrupt" enemies. Core-tactics include injecting false material onto the Internet in order to destroy the reputation of targets and manipulating online discourse and activism for which methods such as posting material to the Internet and falsely attributing it to someone else, pretending to be a victim of the target individual whose reputation is intended to be destroyed and posting "negative information" on various forums may be used.
Known as "Effects" operations, the work of JTRIG had become a "major part" of GCHQ's operations by 2010. The unit's online propaganda efforts (named "Online Covert Action") utilize "mass messaging" and the "pushing [of] stories" via the medium of Twitter, Flickr, Facebook and YouTube. Online "false flag" operations are also used by JTRIG against targets. JTRIG have also changed photographs on social media sites, as well as emailing and texting colleagues and neighbours with "unsavory information" about the targeted individual. In June 2015, NSA files published by Glenn Greenwald revealed new details about JTRIG's work at covertly manipulating online communities. The disclosures also revealed the technique of "credential harvesting", in which journalists could be used to disseminate information and identify non-British journalists who, once manipulated, could give information to the intended target of a secret campaign, perhaps providing access during an interview. It is unknown whether the journalists would be aware that they were being manipulated.
Furthermore, Russia is frequently accused of financing "trolls" to post pro-Russian opinions across the Internet. The Internet Research Agency has become known for employing hundreds of Russians to post propaganda online under fake identities in order to create the illusion of massive support. In 2016 Russia was accused of sophisticated propaganda campaigns to spread fake news with the goal of punishing Democrat Hillary Clinton and helping Republican Donald Trump during the 2016 presidential election as well as undermining faith in American democracy.
In a 2017 report Facebook publicly stated that its site has been exploited by governments for the manipulation of public opinion in other countries – including during the presidential elections in the US and France. It identified three main components involved in an information operations campaign: targeted data collection, content creation and false amplification and includes stealing and exposing information that's not public; spreading stories, false or real, to third parties through fake accounts; and fake accounts being coordinated to manipulate political discussion, such as amplifying some voices while repressing others.
In politics
In 2016 Andrés Sepúlveda disclosed that he manipulated public opinion to rig elections in Latin America. According to him with a budget of $600,000 he led a team of hackers that stole campaign strategies, manipulated social media to create false waves of enthusiasm and derision, and installed spyware in opposition offices to help Enrique Peña Nieto, a right-of-center candidate, win the election.
In the run up to India's 2014 elections, both the Bharatiya Janata party (BJP) and the Congress party were accused of hiring "political trolls" to talk favourably about them on blogs and social media.
The Chinese government is also believed to run a so-called "50-cent army" (a reference to how much they are said to be paid) and the "Internet Water Army" to reinforce favourable opinion towards it and the Communist Party of China (CCP) as well as to suppress dissent.
In December 2014 the Ukrainian information ministry was launched to counter Russian propaganda with one of its first tasks being the creation of social media accounts (also known as the i-Army) and amassing friends posing as residents of eastern Ukraine.
Twitter suspended a number of bot accounts that appeared to be spreading pro-Saudi Arabian tweets about the disappearance of Saudi dissident journalist Jamal Khashoggi.
In business and marketing
Trolling and other applications
In April 2009, Internet trolls of 4chan voted Christopher Poole, founder of the site, as the world's most influential person of 2008 with 16,794,368 votes by an open Internet poll conducted by Time magazine. The results were questioned even before the poll completed, as automated voting programs and manual ballot stuffing were used to influence the vote. 4chan's interference with the vote seemed increasingly likely, when it was found that reading the first letter of the first 21 candidates in the poll spelled out a phrase containing two 4chan memes: "Marblecake. Also, The Game".
Jokesters and politically oriented hacktivists may share sophisticated knowledge of how to manipulate the Web and social media.
Countermeasures
In Wired it was noted that nation-state rules such as compulsory registration and threats of punishment are not adequate measures to combat the problem of online bots.
To guard against the issue of prior ratings influencing perception several websites such as Reddit have taken steps such as hiding the vote-count for a specified time.
Some other potential measures under discussion are flagging posts for being likely satire or false. For instance in December 2016 Facebook announced that disputed articles will be marked with the help of users and outside fact checkers. The company seeks ways to identify 'information operations' and fake accounts and suspended 30,000 accounts before the presidential election in France in a strike against information operations.
Inventor of the World Wide Web Tim Berners-Lee considers putting few companies in charge of deciding what is or isn't true a risky proposition and states that openness can make the web more truthful. As an example he points to Wikipedia which, while not being perfect, allows anyone to edit with the key to its success being not just the technology but also the governance of the site. Namely, it has an army of countless volunteers and ways of determining what is or isn't true.
Furthermore, various kinds of software may be used to combat this problem such as fake checking software or voluntary browser extensions that store every website one reads or use the browsing history to deliver fake revelations to those who read a fake story after some kind of consensus was found on the falsehood of a story.
Furthermore, Daniel Suarez asks society to value critical analytic thinking and suggests education reforms such as the introduction of 'formal logic' as a discipline in schools and training in media literacy and objective evaluation.
Government responses
According
to a study of the Oxford Internet Institute, at least 43 countries
around the globe have proposed or implemented regulations specifically
designed to tackle different aspects of influence campaigns, including
fake news, social media abuse, and election interference.
Germany
In Germany, during the period preceding the elections in September 2017, all major political parties save AfD publicly announced that they would not use social bots in their campaigns. Additionally, they committed to strongly condemning such usage of online bots.
Moves towards regulation on social media have been made: three German states Hessen, Bavaria, and Saxony-Anhalt proposed in early 2017 a law that would mean social media users could face prosecution if they violate the terms and conditions of a platform. For example, the use of a pseudonym on Facebook, or the creation of fake account, would be punishable by up to one year's imprisonment.
Italy
In early 2018, the Italian Communications Agency AGCOM published a set of guidelines on its website, targeting the elections in March that same year. The six main topics are:
- Political Subjects’s Equal Treatment
- Political Propaganda’s Transparency
- Contents Illicit and Activities Whose Dissemination Is Forbidden (i.e. Polls)
- Social Media Accounts of Public Administrations
- Political Propaganda is Forbidden on Election Day and Day Before
- Recommendations for stronger fact-checking services
France
In November 2018, a law against the manipulation of information was passed in France. The law stipulates that during campaign periods:
- Digital platforms must disclose the amount paid for ads and the names of their authors. Past a certain traffic threshold, platforms are required to have a representative present in France, and must publish the algorithms used.
- An interim judge may pass a legal injunction to halt the spread of fake news swiftly. 'Fake news' must satisfy the following: (a)it must be manifest; (b) it must be disseminated on a massive scale; and (c) lead to a disturbance of the peace or compromise the outcome of an election.
Malaysia
In April 2018, the Malaysian parliament passed the Anti-Fake News Act. It defined fake news as 'news, information, data and reports which is or are wholly or partly false.' This applied to citizens or those working at a digital publication, and imprisonment of up to 6 years was possible. However, the law was repealed after heavy criticism in August 2018.
Kenya
In May 2018, President Uhuru Kenyatta signed into law the Computer and Cybercrimes bill, that criminalised cybercrimes including cyberbullying and cyberespionage. If a person “intentionally publishes false, misleading or fictitious data or misinforms with intent that the data shall be considered or acted upon as authentic,” they are subject to fines and up to two years imprisonment.
Research
German chancellor Angela Merkel has issued the Bundestag to deal with the possibilities of political manipulation by social bots or fake news.