In nuclear physics, the valley of stability (also called the belt of stability, nuclear valley, energy valley, or beta stability valley) is a characterization of the stability of nuclides to radioactivity based on their binding energy. Nuclides are composed of protons and neutrons. The shape of the valley refers to the profile of binding energy as a function of the numbers of neutrons and protons, with the lowest part of the valley corresponding to the region of most stable nuclei. The line of stable nuclides down the center of the valley of stability is known as the line of beta stability. The sides of the valley correspond to increasing instability to beta decay (β− or β+). The decay of a nuclide becomes more energetically favorable the further it is from the line of beta stability. The boundaries of the valley correspond to the nuclear drip lines, where nuclides become so unstable they emit single protons or single neutrons. Regions of instability within the valley at high atomic number also include radioactive decay by alpha radiation or spontaneous fission. The shape of the valley is roughly an elongated paraboloid corresponding to the nuclide binding energies as a function of neutron and atomic numbers.
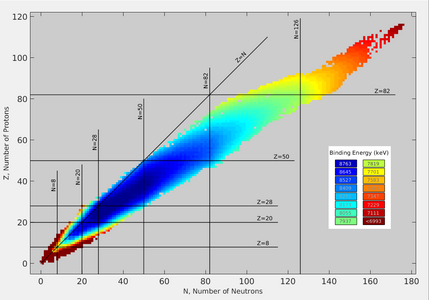
The nuclides within the valley of stability encompass the entire table of nuclides. The chart of those nuclides is known as a Segrè chart, after the physicist Emilio Segrè. The Segrè chart may be considered a map of the nuclear valley. The region of proton and neutron combinations outside of the valley of stability is referred to as the sea of instability.
Scientists have long searched for long-lived heavy isotopes outside of the valley of stability, hypothesized by Glenn T. Seaborg in the late 1960s. These relatively stable nuclides are expected to have particular configurations of "magic" atomic and neutron numbers, and form a so-called island of stability.
Description
All atomic nuclei are composed of protons and neutrons bound together by the nuclear force. There are 286 primordial nuclides that occur naturally on earth, each corresponding to a unique number of protons, called the atomic number, Z, and a unique number of neutrons, called the neutron number, N. The mass number, A, of a nuclide is the sum of atomic and neutron numbers, A = Z + N. Not all nuclides are stable, however. According to Byrne, stable nuclides are defined as those having a half-life greater than 1018 years, and there are many combinations of protons and neutrons that form nuclides that are unstable. A common example of an unstable nuclide is carbon-14 that decays by beta decay into nitrogen-14 with a half-life of about 5,730 years
- 14
6C
→ 14
7N
+
e−
+
ν
e
In this form of decay, the original element becomes a new chemical element in a process known as nuclear transmutation and a beta particle and an electron antineutrino are emitted. An essential property of this and all nuclide decays is that the total energy of the decay product is less than that of the original nuclide. The difference between the initial and final nuclide binding energies is carried away by the kinetic energies of the decay products, often the beta particle and its associated neutrino.
The concept of the valley of stability is a way of organizing all of the nuclides according to binding energy as a function of neutron and proton numbers. Most stable nuclides have roughly equal numbers of protons and neutrons, so the line for which Z = N forms a rough initial line defining stable nuclides. The greater the number of protons, the more neutrons are required to stabilize a nuclide, however, so nuclides with larger values for Z require an even larger number of neutrons, N > Z, to be stable. The valley of stability is formed by the negative of binding energy, the binding energy being the energy required to break apart the nuclide into its proton and neutron components. The stable nuclides have high binding energy, and these nuclides lie along the bottom of the valley of stability. Nuclides with weaker binding energy have combinations of N and Z that lie off of the line of stability and further up the sides of the valley of stability. Unstable nuclides can be formed in nuclear reactors or supernovas, for example. Such nuclides often decay in sequences of reactions called decay chains that take the resulting nuclides sequentially down the slopes of the valley of stability. The sequence of decays take nuclides toward greater binding energies, and the nuclides terminating the chain are stable. The valley of stability provides both a conceptual approach for how to organize the myriad stable and unstable nuclides into a coherent picture and an intuitive way to understand how and why sequences of radioactive decay occur.
Chart of nuclides (isotopes) by binding energy, depicting the valley of stability. The diagonal line corresponds to equal numbers of neutrons and protons. Dark blue squares represent nuclides with the greatest binding energy, hence they correspond to the most stable nuclides. The binding energy is greatest along the floor of the valley of stability.
Chart of nuclides by half life. Black squares represent nuclides with the longest half lives hence they correspond to the most stable nuclides. The most stable, long-lived nuclides lie along the floor of the valley of stability. Nuclides with more than 20 protons must have more neutrons than protons to be stable.
The role of neutrons
The protons and neutrons that comprise an atomic nucleus behave almost identically within the nucleus. The approximate symmetry of isospin treats these particles as identical, but in a different quantum state. This symmetry is only approximate, however, and the nuclear force that binds nucleons together is a complicated function depending on nucleon type, spin state, electric charge, momentum, etc. and with contributions from non-central forces. The nuclear force is not a fundamental force of nature, but a consequence of the residual effects of the strong force that surround the nucleons. One consequence of these complications is that although deuterium, a bound state of a proton (p) and a neutron (n) is stable, exotic nuclides such as diproton or dineutron are unbound. The nuclear force is not sufficiently strong to form either p-p or n-n bound states, or equivalently, the nuclear force does not form a potential well deep enough to bind these identical nucleons.
Stable nuclides require approximately equal numbers of protons and neutrons. The stable nuclide carbon-12 (12C) is composed of six neutrons and six protons, for example. Protons have a positive charge, hence within a nuclide with many protons there are large repulsive forces between protons arising from the Coulomb force. By acting to separate protons from one another, the neutrons within a nuclide play an essential role in stabilizing nuclides. With increasing atomic number, even greater numbers of neutrons are required to obtain stability. The heaviest stable element, lead (Pb), has many more neutrons than protons. The stable nuclide 206Pb has Z = 82 and N = 124, for example. For this reason, the valley of stability does not follow the line Z = N for A larger than 40 (Z = 20 is the element calcium). Neutron number increases along the line of beta stability at a faster rate than atomic number.
The line of beta stability follows a particular curve of neutron–proton ratio, corresponding to the most stable nuclides. On one side of the valley of stability, this ratio is small, corresponding to an excess of protons over neutrons in the nuclides. These nuclides tend to be unstable to β+ decay or electron capture, since such decay converts a proton to a neutron. The decay serves to move the nuclides toward a more stable neutron-proton ratio. On the other side of the valley of stability, this ratio is large, corresponding to an excess of neutrons over protons in the nuclides. These nuclides tend to be unstable to β− decay, since such decay converts neutrons to protons. On this side of the valley of stability, β− decay also serves to move nuclides toward a more stable neutron-proton ratio.
Neutrons, protons, and binding energy
The mass of an atomic nucleus is given by
where and are the rest mass of a proton and a neutron, respectively, and is the total binding energy of the nucleus. The mass–energy equivalence is used here. The binding energy is subtracted from the sum of the proton and neutron masses because the mass of the nucleus is less than that sum. This property, called the mass defect, is necessary for a stable nucleus; within a nucleus, the nuclides are trapped by a potential well. A semi-empirical mass formula states that the binding energy will take the form
The difference between the mass of a nucleus and the sum of the masses of the neutrons and protons that comprise it is known as the mass defect. EB is often divided by the mass number to obtain binding energy per nucleon for comparisons of binding energies between nuclides. Each of the terms in this formula has a theoretical basis. The coefficients , , , and a coefficient that appears in the formula for are determined empirically.
The binding energy expression gives a quantitative estimate for the neutron-proton ratio. The energy is a quadratic expression in Z that is minimized when the neutron-proton ratio is . This equation for the neutron-proton ratio shows that in stable nuclides the number of neutrons is greater than the number of protons by a factor that scales as .
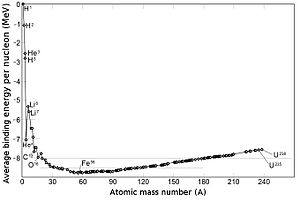
The figure at right shows the average binding energy per nucleon as a function of atomic mass number along the line of beta stability, that is, along the bottom of the valley of stability. For very small atomic mass number (H, He, Li), binding energy per nucleon is small, and this energy increases rapidly with atomic mass number. Nickel-62 (28 protons, 34 neutrons) has the highest mean binding energy of all nuclides, while iron-58 (26 protons, 32 neutrons) and iron-56 (26 protons, 30 neutrons) are a close second and third. These nuclides lie at the very bottom of the valley of stability. From this bottom, the average binding energy per nucleon slowly decreases with increasing atomic mass number. The heavy nuclide 238U is not stable, but is slow to decay with a half-life of 4.5 billion years. It has relatively small binding energy per nucleon.
For β− decay, nuclear reactions have the generic form
- A
ZX
→ A
Z+1X′
+
e−
+
ν
e
where A and Z are the mass number and atomic number of the decaying nucleus, and X and X′ are the initial and final nuclides, respectively. For β+ decay, the generic form is
- A
ZX
→ A
Z−1X′
+
e+
+
ν
e
These reactions correspond to the decay of a neutron to a proton, or the decay of a proton to a neutron, within the nucleus, respectively. These reactions begin on one side or the other of the valley of stability, and the directions of the reactions are to move the initial nuclides down the valley walls towards a region of greater stability, that is, toward greater binding energy.
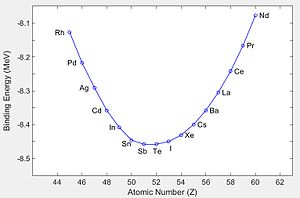
The figure at right shows the average binding energy per nucleon across the valley of stability for nuclides with mass number A = 125. At the bottom of this curve is tellurium (52Te), which is stable. Nuclides to the left of 52Te are unstable with an excess of neutrons, while those on the right are unstable with an excess of protons. A nuclide on the left therefore undergoes β− decay, which converts a neutron to a proton, hence shifts the nuclide to the right and toward greater stability. A nuclide on the right similarly undergoes β+ decay, which shifts the nuclide to the left and toward greater stability.
Heavy nuclides are susceptible to α decay, and these nuclear reactions have the generic form,
- A
ZX
→ A-4
Z-2X′
+ 4
2He
As in β decay, the decay product X′ has greater binding energy and it is closer to the middle of the valley of stability. The α particle carries away two neutrons and two protons, leaving a lighter nuclide. Since heavy nuclides have many more neutrons than protons, α decay increases a nuclide's neutron-proton ratio.
Proton and neutron drip lines
The boundaries of the valley of stability, that is, the upper limits of the valley walls, are the neutron drip line on the neutron-rich side, and the proton drip line on the proton-rich side. The nucleon drip lines are at the extremes of the neutron-proton ratio. At neutron–proton ratios beyond the drip lines, no nuclei can exist. The location of the neutron drip line is not well known for most of the Segrè chart, whereas the proton and alpha drip lines have been measured for a wide range of elements. Drip lines are defined for protons, neutrons, and alpha particles, and these all play important roles in nuclear physics.
The difference in binding energy between neighboring nuclides increases as the sides of the valley of stability are ascended, and correspondingly the nuclide half-lives decrease, as indicated in the figure above. If one were to add nucleons one at a time to a given nuclide, the process will eventually lead to a newly formed nuclide that is so unstable that it promptly decays by emitting a proton (or neutron). Colloquially speaking, the nucleon has 'leaked' or 'dripped' out of the nucleus, hence giving rise to the term "drip line".
Proton emission is not seen in naturally occurring nuclides. Proton emitters can be produced via nuclear reactions, usually utilizing linear particle accelerators (linac). Although prompt (i.e. not beta-delayed) proton emission was observed from an isomer in cobalt-53 as early as 1969, no other proton-emitting states were found until 1981, when the proton radioactive ground states of lutetium-151 and thulium-147 were observed at experiments at the GSI in West Germany. Research in the field flourished after this breakthrough, and to date more than 25 nuclides have been found to exhibit proton emission. The study of proton emission has aided the understanding of nuclear deformation, masses and structure, and it is an example of quantum tunneling.
Two examples of nuclides that emit neutrons are beryllium-13 (mean life 2.7×10−21 s) and helium-5 (7×10−22 s). Since only a neutron is lost in this process, the atom does not gain or lose any protons, and so it does not become an atom of a different element. Instead, the atom will become a new isotope of the original element, such as beryllium-13 becoming beryllium-12 after emitting one of its neutrons.
In nuclear engineering, a prompt neutron is a neutron immediately emitted by a nuclear fission event. Prompt neutrons emerge from the fission of an unstable fissionable or fissile heavy nucleus almost instantaneously. Delayed neutron decay can occur within the same context, emitted after beta decay of one of the fission products. Delayed neutron decay can occur at times from a few milliseconds to a few minutes. The U.S. Nuclear Regulatory Commission defines a prompt neutron as a neutron emerging from fission within 10−14 seconds.
Island of stability
The island of stability is a region outside the valley of stability where it is predicted that a set of heavy isotopes with near magic numbers of protons and neutrons will locally reverse the trend of decreasing stability in elements heavier than uranium. The hypothesis for the island of stability is based upon the nuclear shell model, which implies that the atomic nucleus is built up in "shells" in a manner similar to the structure of the much larger electron shells in atoms. In both cases, shells are just groups of quantum energy levels that are relatively close to each other. Energy levels from quantum states in two different shells will be separated by a relatively large energy gap. So when the number of neutrons and protons completely fills the energy levels of a given shell in the nucleus, the binding energy per nucleon will reach a local maximum and thus that particular configuration will have a longer lifetime than nearby isotopes that do not possess filled shells.
A filled shell would have "magic numbers" of neutrons and protons. One possible magic number of neutrons for spherical nuclei is 184, and some possible matching proton numbers are 114, 120 and 126. These configurations imply that the most stable spherical isotopes would be flerovium-298, unbinilium-304 and unbihexium-310. Of particular note is 298Fl, which would be "doubly magic" (both its proton number of 114 and neutron number of 184 are thought to be magic). This doubly magic configuration is the most likely to have a very long half-life. The next lighter doubly magic spherical nucleus is lead-208, the heaviest known stable nucleus and most stable heavy metal.
Discussion
The valley of stability can be helpful in interpreting and understanding properties of nuclear decay processes such as decay chains and nuclear fission.
Radioactive decay often proceeds via a sequence of steps known as a decay chain. For example, 238U decays to 234Th which decays to 234mPa and so on, eventually reaching 206Pb:
With each step of this sequence of reactions, energy is released and the decay products move further down the valley of stability towards the line of beta stability. 206Pb is stable and lies on the line of beta stability.
The fission processes that occur within nuclear reactors are accompanied by the release of neutrons that sustain the chain reaction. Fission occurs when a heavy nuclide such as uranium-235 absorbs a neutron and breaks into lighter components such as barium or krypton, usually with the release of additional neutrons. Like all nuclides with a high atomic number, these uranium nuclei require many neutrons to bolster their stability, so they have a large neutron-proton ratio (N/Z). The nuclei resulting from a fission (fission products) inherit a similar N/Z, but have atomic numbers that are approximately half that of uranium. Isotopes with the atomic number of the fission products and an N/Z near that of uranium or other fissionable nuclei have too many neutrons to be stable; this neutron excess is why multiple free neutrons but no free protons are usually emitted in the fission process, and it is also why many fission product nuclei undergo a long chain of β− decays, each of which converts a nucleus N/Z to (N − 1)/(Z + 1), where N and Z are, respectively, the numbers of neutrons and protons contained in the nucleus.
When fission reactions are sustained at a given rate, such as in a liquid-cooled or solid fuel nuclear reactor, the nuclear fuel in the system produces many antineutrinos for each fission that has occurred. These antineutrinos come from the decay of fission products that, as their nuclei progress down a β− decay chain toward the valley of stability, emit an antineutrino along with each β− particle. In 1956, Reines and Cowan exploited the (anticipated) intense flux of antineutrinos from a nuclear reactor in the design of an experiment to detect and confirm the existence of these elusive particles.















![{\displaystyle {\begin{array}{l}{}\\{\ce {^{238}_{92}U->[\alpha ][4.5\times 10^{9}\ {\ce {y}}]{^{234}_{90}Th}->[\beta ^{-}][24\ {\ce {d}}]{^{234\!m}_{91}Pa}}}{\ce {->[\beta ^{-}][1\ {\ce {min}}]}}{\ce {^{234}_{92}U->[\alpha ][2.4\times 10^{5}\ {\ce {y}}]{^{230}_{90}Th}->[\alpha ][7.7\times 10^{4}\ {\ce {y}}]}}\\{\ce {^{226}_{88}Ra->[\alpha ][1600\ y]{^{222}_{86}Rn}->[\alpha ][3.8\ {\ce {d}}]{^{218}_{84}Po}->[\alpha ][3\ {\ce {min}}]{^{214}_{82}Pb}->[\beta ^{-}][27\ {\ce {min}}]{^{214}_{83}Bi}->[\beta ^{-}][20\ {\ce {min}}]}}\\{\ce {^{214}_{84}Po->[\alpha ][164\ \mu {\ce {s}}]{^{210}_{82}Pb}->[\beta ^{-}][22\ {\ce {y}}]{^{210}_{83}Bi}->[\beta ^{-}][5\ {\ce {d}}]{^{210}_{84}Po}->[\alpha ][138\ {\ce {d}}]{^{206}_{82}Pb}}}\\{}\end{array}}}](https://wikimedia.org/api/rest_v1/media/math/render/svg/ba2b0c735b768ae8bdff71e9622addbc3a6ab68f)


