Bitcoin is a digital asset designed by its pseudonymous inventor, Satoshi Nakamoto, to work as a currency.
Since Bitcoin's first appearance in 2008, it has generated a wide variety of responses and analyses.
Classification
Bitcoin is a digital asset designed by its inventor, Satoshi Nakamoto, to work as a currency. It is commonly referred to with terms like: digital currency, digital cash, virtual currency, electronic currency, digital gold, or cryptocurrency.
The question whether bitcoin is a currency or not is disputed. Bitcoins have three useful qualities in a currency, according to The Economist in January 2015: they are "hard to earn, limited in supply and easy to verify". Economists define money as a store of value, a medium of exchange and a unit of account, and agree that bitcoin has some way to go to meet all these criteria. It does best as a medium of exchange: As of March 2014, the bitcoin market suffered from volatility, limiting the ability of bitcoin to act as a stable store of value, and retailers accepting bitcoin use other currencies as their principal unit of account.
Classification of bitcoin by the United States government is to date unclear with multiple conflicting rulings. In 2013 Judge Amos L. Mazzant III of the United States District Court for the Eastern District of Texas stated that "Bitcoin is a currency or form of money". In July 2016, Judge Teresa Mary Pooler of Eleventh Judicial Circuit Court of Florida cleared Michell Espinoza in State of Florida v. Espinoza in money-laundering charges he faced involving his use of bitcoin. Judge Pooler stated "Bitcoin may have some attributes in common with what we commonly refer to as money, but differ in many important aspects, they are certainly not tangible wealth and cannot be hidden under a mattress like cash and gold bars." In September 2016, a ruling by Judge Alison J. Nathan of United States District Court for the Southern District of New York contradicted the Florida Espinoza ruling stating "Bitcoins are funds within the plain meaning of that term.— Bitcoins can be accepted as a payment for goods and services or bought directly from an exchange with a bank account. They therefore function as pecuniary resources and are used as a medium of exchange and a means of payment." The U.S. Treasury categorizes bitcoin as a decentralized virtual currency. The Commodity Futures Trading Commission classifies bitcoin as a commodity, and the Internal Revenue Service classifies it as an asset.
The South African Revenue Service, the legislation of Canada, the Ministry of Finance of the Czech Republic and several others classify bitcoin as an intangible asset.
The Bundesbank says that bitcoin is not a virtual currency or digital money. It recommends using the term "crypto token".
The People's Bank of China has stated that bitcoin "is fundamentally not a currency but an investment target".
Journalists and academics also debate what to call bitcoin. Some media outlets do make a distinction between "real" money and bitcoins, while others call bitcoin real money. The Wall Street Journal declared it a commodity in December 2013. A Forbes journalist referred to it as digital collectible. Two University of Amsterdam computer scientists proposed the term "money-like informational commodity".
In addition to the above, bitcoin is also characterized as a payment system.
General use
According to research produced by Cambridge University in 2017, there are between 2.9 million and 5.8 million unique users actively using a cryptocurrency wallet, most of them using bitcoin. The number of active users has grown significantly since 2013 (there were 0.3 to 1.3 million unique users at the time).
Buying and selling
Bitcoins can be bought and sold both on- and offline. Participants in online exchanges offer bitcoin buy and sell bids. Using an online exchange to obtain bitcoins entails some risk, and, according to a study published in April 2013, 45% of exchanges fail and take client bitcoins with them. Exchanges have since implemented measures to provide proof of reserves in an effort to convey transparency to users. Offline, bitcoins may be purchased directly from an individual or at a bitcoin ATM. Bitcoin machines are not however traditional ATMs. Bitcoin kiosks are machines connected to the Internet, allowing the insertion of cash in exchange for bitcoins. Bitcoin kiosks do not connect to a bank and may also charge transaction fees as high as 7% and exchange rates US$50 over rates from elsewhere.
As of 2016 it was estimated there were over 800 bitcoin ATMs operating globally, the majority (500+) being in the United States.
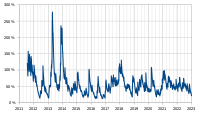
Price and volatility
According to Mark T. Williams, as of 2014, bitcoin has volatility seven times greater than gold, eight times greater than the S&P 500, and 18 times greater than the U.S. dollar.
Attempting to explain the high volatility, a group of Japanese scholars stated that there is no stabilization mechanism. The Bitcoin Foundation contends that high volatility is due to insufficient liquidity, while a Forbes journalist claims that it is related to the uncertainty of its long-term value, and the high volatility of a startup currency makes sense, "because people are still experimenting with the currency to figure out how useful it is."
There are uses where volatility does not matter, such as online gambling, tipping, and international remittances. As of 2014, pro-bitcoin venture capitalists argued that the greatly increased trading volume that planned high-frequency trading exchanges would generate is needed to decrease price volatility.
The price of bitcoins has gone through various cycles of appreciation and depreciation referred to by some as bubbles and busts. In 2011, the value of one bitcoin rapidly rose from about US$0.30 to US$32 before returning to US$2. In the latter half of 2012 and during the 2012–13 Cypriot financial crisis, the bitcoin price began to rise, reaching a high of US$266 on 10 April 2013, before crashing to around US$50. On 29 November 2013, the cost of one bitcoin rose to the all-time peak of US$1,242. Some evidence suggests that part of this peak in the price of bitcoin was due to price manipulation. In 2014, the price fell sharply, and as of April remained depressed at little more than half 2013 prices. As of August 2014 it was under US$600.
In January 2015, noting that the bitcoin price had dropped to its lowest level since spring 2013 – around US$224 – The New York Times suggested that "[w]ith no signs of a rally in the offing, the industry is bracing for the effects of a prolonged decline in prices. In particular, bitcoin mining companies, which are essential to the currency's underlying technology, are flashing warning signs." Also in January 2015, Business Insider reported that deep web drug dealers were "freaking out" as they lost profits through being unable to convert bitcoin revenue to cash quickly enough as the price declined – and that there was a danger that dealers selling reserves to stay in business might force the bitcoin price down further.
Economic theory suggests that the volatility of the price of bitcoin will drop when business and consumer usage of bitcoin increases. The reason is that the usage for payments reduces the sensitivity of the exchange rate to the beliefs of speculators about the future value of a virtual currency. According to The Wall Street Journal, as of April 2016, bitcoin is starting to look slightly more stable than gold. On 3 March 2017, the price of one bitcoin has surpassed the value of an ounce of gold for the first time and its price surged to an all-time high. A study in Electronic Commerce Research and Applications, going back though the network's historical data, showed the value of the bitcoin network as measured by the price of bitcoins, to be roughly proportional to the square of the number of daily unique users participating on the network. This is a form of Metcalfe's law and suggests that the network was demonstrating network effects proportional to its level of user adoption.
As a speculative bubble
Bitcoin has been characterized as a speculative bubble by eight laureates of the Nobel Memorial Prize in Economic Sciences: Paul Krugman, Robert J. Shiller, Joseph Stiglitz, Richard Thaler, James Heckman, Thomas Sargent, Angus Deaton, and Oliver Hart; and by central bank officials including Alan Greenspan, Ben Bernanke, Janet Yellen, Agustín Carstens, Vítor Constâncio, and Nout Wellink.
The investors Warren Buffett and George Soros have respectively characterized it as a "mirage" and a "bubble"; while the business executive Jack Ma has called it a "bubble".
Views of economists
In 2014, Nobel laureate Robert J. Shiller stated that bitcoin "exhibited many of the characteristics of a speculative bubble"; in 2017, Shiller wrote that bitcoin was the best current example of a speculative bubble.
Economist John Quiggin in 2013 said "bitcoins are the most demonstrably valueless financial asset ever created".
Researchers Neil Gandal, JT Hamrick, Tyler Moore, and Tali Oberman claimed that in late 2013, price manipulation by one person likely caused a price spike from US$150 to more than US$1000.
Nobel laureate Joseph Stiglitz in 2017 said "It’s a bubble that’s going to give a lot of people a lot of exciting times as it rides up and then goes down." He emphasized its use by criminals, its lack of a socially useful purpose, and said that it should be outlawed.
Nobel laureate Paul Krugman wrote in 2018 that bitcoin is "a bubble wrapped in techno-mysticism inside a cocoon of libertarian ideology". He criticized it as a very slow and expensive means of payment, used mostly to buy blackmarket goods, without a "tether to reality".
Nobel laureate Richard Thaler emphasizes the irrationality in the bitcoin market that has led to the bubble, demonstrating the irrationality with the example of firms that have added the word blockchain to their names which have then had large increases in their stock price. The extremely high volatility in bitcoin's price also is due to irrationality according to Thaler.
Four Nobel laureates, James Heckman, Thomas Sargent, Angus Deaton, and Oliver Hart, characterized bitcoin as a bubble at a joint press conference in 2018. Hart cited Christopher Sims's work showing no intrinsic value to bitcoin. Heckman compared bitcoin to the tulip bubble. Deaton pointed to bitcoin's use by criminals.
Professor Nouriel Roubini of New York University has called bitcoin the "mother of all bubbles", writing that the underlying blockchain technology has "massive obstacles standing in its way", including a lack of "common and universal protocols" of the kind that enabled the early Internet. According to Roubini, bitcoin has failed as a unit of account, a means of payment, and as a store of value; he calls the claim that bitcoin cannot be debased "fraudulent". "Scammers, swindlers, charlatans, and carnival barkers (all conflicted insiders) have tapped into clueless retail investors' FOMO ('fear of missing out'), and taken them for a ride," he writes.
Views of central bank officials
Early claims that bitcoin was a bubble focused on the lack of any intrinsic value of bitcoin. These claims include that of former Federal Reserve Chairman Alan Greenspan in 2013. He stated "You really have to stretch your imagination to infer what the intrinsic value of Bitcoin is. I haven't been able to do it."
In 2017 Greenspan compared bitcoin to the Continental dollar, which ultimately collapsed. He said "Humans buy all sorts of things that aren't worth anything. People gamble in casinos when the odds are against them. It has never stopped anybody."
Former Fed Chair Ben Bernanke (in 2015) and outgoing Fed Chair Janet Yellen (in 2017) have both expressed concerns about the stability of bitcoin's price and its lack of use as a medium of transactions.
Agustín Carstens, head of the Bank of International Settlements, has called bitcoin "a combination of a bubble, a Ponzi scheme and an environmental disaster", and warned of cryptocurrencies undermining public trust in the financial system.
David Andolfatto, a vice president at the Federal Reserve Bank of St. Louis, stated, "Is bitcoin a bubble? Yes, if bubble is defined as a liquidity premium." According to Andolfatto, the price of bitcoin "consists purely of a bubble".
Comparisons of bitcoin to the tulip mania of seventeenth-century Holland have been made by the vice-president of the European Central Bank, Vítor Constâncio and by former president of the Dutch Central Bank, Nout Wellink. In 2013, Wellink remarked, "This is worse than the tulip mania ... At least then you got a tulip [at the end], now you get nothing."
Views of investors and executives
American investor Warren Buffett warned investors about bitcoin in 2014, "Stay away from it. It's a mirage, basically." He repeated the warning in 2018 calling bitcoin "probably rat poison squared". He believes that bitcoin is a non-productive asset. "When you're buying nonproductive assets, all you're counting on is the next person is going to pay you more because they're even more excited about another next person coming along."
Buffett's close associate Charlie Munger is even more direct in his disdain. Trading cryptocurrencies is "just dementia" according to Munger. Bitcoin is "worthless" and a "turd".
John Bogle, the founder of The Vanguard Group, is also very direct "Avoid bitcoin like the plague. Did I make myself clear? .... There is nothing to support bitcoin except the hope that you will sell it to someone for more than you paid for it."
George Soros, answering an audience question after a speech in Davos, Switzerland, in 2018, said that cryptocurrencies are not a store of value but are an economic bubble. Nevertheless, they may not crash due to the rising influence of dictators trying to "build a nest egg abroad".
James Chanos, known as the "dean of the short sellers", believes that bitcoin and other cryptocurrencies are a mania and useful only for tax avoidance or otherwise hiding income from the government. Bitcoin "is simply a security speculation game masquerading as a technological breakthrough in monetary policy".
Two lead software developers of bitcoin, Gavin Andresen and Mike Hearn, have warned that bubbles may occur.
On 13 September 2017, Jamie Dimon referred to bitcoin to as a "fraud", comparing it to pyramid schemes, and stated that JPMorgan Chase would fire employees trading while the company released a report critical of the cryptocurrency. However, in a January 2018 interview Jamie Dimon voiced regrets about his earlier bitcoin remarks, and noted "The blockchain is real, You can have cryptodollars in yen and stuff like that. ICOs ... you got to look at everyone individually."
Alibaba chairman Jack Ma stated in 2018, "There is no bubble for blockchain, but there's a bitcoin bubble"[60] and "[blockchain] technology itself isn’t the bubble, but bitcoin likely is".
Fraud concerns
Some journalists, economists, and the central bank of Estonia have voiced concerns that bitcoin is a Ponzi scheme. In 2013, Eric Posner, a law professor at the University of Chicago, stated that "a real Ponzi scheme takes fraud; bitcoin, by contrast, seems more like a collective delusion." In 2014 reports by both the World Bank and the Swiss Federal Council examined the concerns and came to the conclusion that bitcoin is not a Ponzi scheme. In 2017 billionaire Howard Marks referred to bitcoin as a pyramid scheme.
On 12 September 2017, Jamie Dimon, CEO of JPMorgan Chase, called bitcoin a "fraud" and said he would fire anyone in his firm caught trading it. Zero Hedge claimed that the same day Dimon made his statement, JP Morgan also purchased a large amount of bitcoins for its clients.
Value forecasts
Financial journalists and analysts, economists, and investors have attempted to predict the possible future value of bitcoin. In April 2013, economist John Quiggin stated, "bitcoins will attain their true value of zero sooner or later, but it is impossible to say when". A similar forecast was made in November 2014 by economist Kevin Dowd.
In December 2013, finance professor Mark T. Williams forecast that bitcoin would trade for less than $10 by mid-year 2014. In the indicated period bitcoin has exchanged as low as $344 (April 2014) and during July 2014 the bitcoin low was $609. In December 2014, Williams said, "The probability of success is low, but if it does hit, the reward will be very large."
In November 2014, David Yermack, Professor of Finance at New York University Stern School of Business, forecast that in November 2015 bitcoin may be all but worthless. In the indicated period bitcoin has exchanged as low as $176.50 (January 2015) and during November 2015 the bitcoin low was $309.90.
In May 2013, Bank of America FX and Rate Strategist David Woo forecast a maximum fair value per bitcoin of $1,300. Bitcoin investor Cameron Winklevoss stated in December 2013 that the "small bull case scenario for bitcoin is... 40,000 USD a coin".
Obituaries
The "death" of bitcoin has been proclaimed numerous times. One journalist has recorded 29 such "obituaries" as of early 2015.
Forbes magazine declared bitcoin "dead" in June 2011, followed by Gizmodo Australia in August 2011. Wired magazine wrote it had "expired" in December 2012. Ouishare Magazine declared, "game over, bitcoin" in May 2013, and New York Magazine stated bitcoin was "on its path to grave" in June 2013. Reuters published an "obituary" for bitcoin in January 2014. Street Insider declared bitcoin "dead" in February 2014, followed by The Weekly Standard in March 2014, Salon in March 2014, Vice News in March 2014, and Financial Times in September 2014. In January 2015, USA Today stated bitcoin was "headed to the ash heap", and The Telegraph declared "the end of bitcoin experiment". In January 2016, former bitcoin developer Mike Hearn called bitcoin a "failed project".
Peter Greenhill, Director of E-Business Development for the Isle of Man, commenting on the obituaries paraphrased Mark Twain saying "reports of bitcoin's death have been greatly exaggerated".
Reception
Some economists have responded positively to bitcoin while others have expressed skepticism. François R. Velde, Senior Economist at the Chicago Fed, described it as "an elegant solution to the problem of creating a digital currency". Paul Krugman and Brad DeLong have found fault with bitcoin, questioning why it should act as a reasonably stable store of value or whether there is a floor on its value. Economist John Quiggin has criticized bitcoin as "the final refutation of the efficient-market hypothesis".
David Andolfatto, Vice President at the Federal Reserve Bank of St. Louis, stated that bitcoin is a threat to the establishment, which he argues is a good thing for the Federal Reserve System and other central banks, because it prompts these institutions to operate sound policies.
Free software movement activist Richard Stallman has criticized the lack of anonymity and called for reformed development. PayPal President David A. Marcus calls bitcoin a "great place to put assets" but claims it will not be a currency until price volatility is reduced. Bill Gates, in relation to the cost of moving money from place to place in an interview for Bloomberg L.P. stated: "Bitcoin is exciting because it shows how cheap it can be."
In November 2013, three US government officials testified at senate hearings that "Bitcoin has legitimate uses". According to The Washington Post, "Most of the other witnesses echoed those sentiments."
Acceptance by merchants
Most bitcoin transactions take place on a cryptocurrency exchange, rather than being used in transactions with merchants. Delays processing payments through the blockchain of about ten minutes make bitcoin use very difficult in a retail setting. Prices are not usually quoted in units of bitcoin and many trades involve one, or sometimes two, conversions into conventional currencies. Merchants that do accept bitcoin payments may use payment service providers to perform the conversions.
In 2017 and 2018 bitcoin's acceptance among major online retailers included only three of the top 500 U.S. online merchants, down from five in 2016. Reasons for this decline include high transaction fees due to bitcoin's scalability issues and long transaction times.
Bloomberg reported that the largest 17 crypto merchant-processing services handled $69 million in June 2018, down from $411 million in September 2017. Bitcoin is "not actually usable" for retail transactions because of high costs and the inability to process chargebacks, according to Nicholas Weaver, a researcher quoted by Bloomberg. High price volatility and transaction fees make paying for small retail purchases with bitcoin impractical, according to economist Kim Grauer.
Bitcoin started to be accepted also for real estate payments in late 2017. The first recorded sale of a house in exchange for bitcoin happened in September 2017, when Texas based Kuper Sotheby's International Realty brokered the deal using bitpay.com to process the payment.
Two months later, a first recorded sale of apartment in the world and first real estate property in Europe was sold for bitcoin in November 2017 in the Czech republic. The Czech real estate agency HOME Hunters brokered a deal of a three-room apartment for a Russian buyer without using a payment service providers at all.
Some U.S. political candidates, including New York City Democratic Congressional candidate Jeff Kurzon have said they would accept campaign donations in bitcoin.
Payment service providers
Merchants accepting bitcoin, such as Dish Network, use the services of bitcoin payment service providers such as BitPay or Coinbase. When a customer pays in bitcoin, the payment service provider accepts the bitcoin on behalf of the merchant, directly converts it, and sends the obtained amount to merchant's bank account, charging a fee of less than 1 percent for the service.
Use in retail transactions
Due to the design of bitcoin, all retail figures are only estimates. According to Tim Swanson, head of business development at a Hong Kong-based cryptocurrency technology company, in 2014, daily retail purchases made with bitcoin were worth about $2.3 million. MIT Technology review estimates that, as of February 2015, fewer than 5,000 bitcoins per day (worth roughly $1.2 million at the time) were being used for retail transactions, and concludes that in 2014 "it appears there has been very little if any increase in retail purchases using bitcoin."
Financial institutions
Bitcoin companies have had difficulty opening traditional bank accounts because lenders have been leery of bitcoin's links to illicit activity. According to Antonio Gallippi, a co-founder of BitPay, "banks are scared to deal with bitcoin companies, even if they really want to". In 2014, the National Australia Bank closed accounts of businesses with ties to bitcoin, and HSBC refused to serve a hedge fund with links to bitcoin. Australian banks in general have been reported as closing down bank accounts of operators of businesses involving the currency; this has become the subject of an investigation by the Australian Competition & Consumer Commission. Nonetheless, Australian banks have adopted the blockchain technology on which bitcoin is based.
In September 2019 the Central Bank of Venezuela, at the request of PDVSA, ran tests to determine if bitcoin and Ethereum could be held in central bank's reserves. The request was motivated by oil company's goal to pay its suppliers.
As an investment
Some Argentinians have bought bitcoins to protect their savings against high inflation or the possibility that governments could confiscate savings accounts. During the 2012–2013 Cypriot financial crisis, bitcoin purchases in Cyprus rose due to fears that savings accounts would be confiscated or taxed.
Other methods of investment are bitcoin funds. The first regulated bitcoin fund was established in Jersey in July 2014 and approved by the Jersey Financial Services Commission. Also, c. 2012 an attempt was made by Cameron and Tyler Winklevoss (who in April 2013 claimed they owned nearly 1% of all bitcoins in existence) to establish a bitcoin ETF. As of 10 March 2017 the bitcoin ETF was declined by the SEC because of regulatory concerns. The price fell 15% in a few minutes, but soon mostly recovered. As of early 2015, they have announced plans to launch a New York-based bitcoin exchange named Gemini, which has received approval to launch on 5 October 2015. On 4 May 2015, Bitcoin Investment Trust started trading on the OTCQX market as GBTC.
In 2013 and 2014, the European Banking Authority and the Financial Industry Regulatory Authority (FINRA), a United States self-regulatory organization, warned that investing in bitcoins carries significant risks. Forbes named bitcoin the best investment of 2013. In 2014, Bloomberg named bitcoin one of its worst investments of the year. In 2015, bitcoin topped Bloomberg's currency tables.
To improve access to price information and increase transparency, on 30 April 2014 Bloomberg LP announced plans to list prices from bitcoin companies Kraken and Coinbase on its 320,000 subscription financial data terminals. In May 2015, Intercontinental Exchange Inc., parent company of the New York Stock Exchange, announced a bitcoin index initially based on data from Coinbase transactions.
According to Bloomberg, in 2013 there were about 250 bitcoin wallets with more than $1 million worth of bitcoins. The number of bitcoin millionaires is uncertain as people can have more than one wallet.
Venture capital
Venture capitalists, such as Peter Thiel's Founders Fund, which invested US$3 million in BitPay, do not purchase bitcoins themselves, instead funding bitcoin infrastructure like companies that provide payment systems to merchants, exchanges, wallet services, etc. In 2012, an incubator for bitcoin-focused start-ups was founded by Adam Draper, with financing help from his father, venture capitalist Tim Draper, one of the largest bitcoin holders after winning an auction of 30,000 bitcoins, at the time called 'mystery buyer'. The company's goal is to fund 100 bitcoin businesses within 2–3 years with $10,000 to $20,000 for a 6% stake. Investors also invest in bitcoin mining. According to a 2015 study by Paolo Tasca, bitcoin startups raised almost $1 billion in three years (Q1 2012 – Q1 2015).
Crowdfunding
Bitcoin is useful for crowdfunding. For example, one college football sign netted over $20,000 in donations for a bitcoin enthusiast. He was shown by local TV company with a broadsheet "Hi mom, send bitcoins".
Political economy
The decentralization of money offered by virtual currencies like bitcoin has its theoretical roots in the Austrian school of economics such as subjective theory of value, especially with Friedrich von Hayek in his book Denationalisation of Money: The Argument Refined, in which he advocates a complete free market in the production, distribution and management of money to end the monopoly of central banks.
Bitcoin appeals to tech-savvy libertarians, because it so far exists outside the institutional banking system and the control of governments. However, researchers looking to uncover the reasons for interest in bitcoin did not find evidence in Google search data that this was linked to libertarianism.
Bitcoin's appeal reaches from left wing critics, "who perceive the state and banking sector as representing the same elite interests, ... recognising in it the potential for collective direct democratic governance of currency" and socialists proposing their "own states, complete with currencies", to right wing critics suspicious of big government, at a time when activities within the regulated banking system were responsible for the severity of the financial crisis of 2007–08, "because governments are not fully living up to the responsibility that comes with state-sponsored money". Two WSJ journalists describe bitcoin in their book as "about freeing people from the tyranny of centralised trust".