Universal Serial Bus (USB) is an industry standard that specifies the physical interfaces and protocols for connecting, data transferring and powering of hosts, such as personal computers, peripherals, e.g. keyboards and mobile devices, and intermediate hubs. USB was designed to standardize the connection of peripherals to computers, replacing various interfaces such as serial ports, parallel ports, game ports, and ADB ports. It has become commonplace on a wide range of devices, such as keyboards, mice, cameras, printers, scanners, flash drives, smartphones, game consoles, and power banks.
As of 2023, USB consists of four generations of specifications: USB 1.‘‘x’’, USB 2.0, USB 3.‘‘x’’, and USB4. Since USB4 the specification enhances the data transfer and power supply functionality with
connection-oriented, tunneling architecture designed to combine multiple protocols onto a single physical interface, so that the total speed and performance of the USB4 Fabric can be dynamically shared.
USB4 particularly supports the tunneling of the Thunderbolt 3 protocols, namely PCI Express (PCIe, load/store interface) and DisplayPort. USB4 also adds host-to-host interfaces.
Each specification subversion supports different maximum signaling rates from 1.5 Mbit/s in USB 1.0 to 80 Gbit/s in USB4. USB also provides power supply to peripheral devices; the latest versions of the standard extend the power delivery limits for battery charging and devices requiring up to 240 watts (USB Power Delivery (USB-PD)). Over the years USB(-PD) has been adopted as the standard power supply and charging format for many mobile devices, such as mobile phones, reducing the need for proprietary chargers.
USB connector interfaces are classified into three types: A (host), B (peripheral), and C (2014, replaces A and B). The A and B types know different sizes: Standard, Mini, and Micro. The standard size is the largest and is mainly used for desktop and larger peripheral equipment. The mini size was introduced for mobile devices, but it was replaced by the thinner micro size. The micro size is nowadays the most common for smartphones and tablets. The USB Type-C connector interface is the newest and the only one applicable to USB4. It is reversible and can support various functionalities and protocols; some are mandatory, many just optional, and depending on the type of the device: host, peripheral device, or hub.
Since the USB 1.1 specification fully replaces the USB 1.0 specification, and since the USB 3.2 specification fully replaces the USB 3.1 (and therefore the USB 3.0 specification as well), and since USB 2.0 is backward-compatible with USB 1.0/1.1, and since the USB 3.x specifications include the USB 2.0 specification, and since USB4 "functionally replaces" the USB 3.2 specification "while retaining USB 2.0 bus operating in parallel", backward-compatibility is always given, but obviously always comes along with a decrease in, both, signaling rates and power rates, and less supported functionalities.
The USB 3.0 specification defined a new architecture and protocol, named SuperSpeed (aka SuperSpeed USB, marketed as SS), which included a new lane for a new signal coding scheme (8b/10b symbols, 5 Gbps; also known as Gen 1) providing full-duplex data transfers that physically required five additional wires and pins, while preserving the USB 2.0-architectur and -protocols and therefore keeping the original 4 pins/wires for the USB 2.0 backward-compatibility resulting in 9 wires (with 9 or 10 pins at connector interfaces; ID-pin is not wired) in total. The USB 3.1 specification introduced an Enhanced SuperSpeed-architecture – while preserving the SuperSpeed-architecture and -protocol – with an additional SuperSpeedPlus-architecture adding a new coding schema (128b/132b symbols, 10 Gbps; also known as Gen 2) and protocol named SuperSpeedPlus (aka SuperSpeedPlus USB, for some time period marketed as SS+). The USB 3.2 specification even added an additional second lane to the Enhanced SuperSpeed-architecture besides other enhancements, so that SuperSpeedPlus USB implements the Gen 1x2, Gen 2x1 and Gen 2x2 operation modes. The SuperSpeed-architecture and -protocol (aka SuperSpeed USB) still implements the one-lane Gen 1x1 operation mode. Therefore, two-lane operations, namely USB 3.2 Gen 1x2 (10 Gbit/s) and Gen 2x2 (20 Gbit/s), are only possible with Full-Featured USB Type-C fabrics (24 pins). As of 2023, they are hardly yet implemented by most products so far. On the other hand, USB 3.2 Gen 1(x1) (5 Gbit/s) and Gen 2(x1) (10 Gbit/s) implementations are quite common now for some years.
Overview
USB was designed to standardize the connection of peripherals to personal computers, both to communicate with and to supply electric power. It has largely replaced interfaces such as serial ports and parallel ports and has become commonplace on a wide range of devices. Examples of peripherals that are connected via USB include computer keyboards and mice, video cameras, printers, portable media players, mobile (portable) digital telephones, disk drives, and network adapters.
USB connectors have been increasingly replacing other types as charging cables of portable devices.
Connector type quick reference
Each USB connection is made using two connectors: a socket (or receptacle) and a plug. In the following table, schematics for only the sockets are shown, although for each there is a corresponding plug (or plugs).
| Standard | USB 1.0 1996 |
USB 1.1 1998 |
USB 2.0 2001 |
USB 2.0 Revised |
USB 3.0 2008 |
USB 3.1 2013 |
USB 3.2 2017 |
USB4 2019 |
USB4 V2.0 2022 |
|---|---|---|---|---|---|---|---|---|---|
| Maximum signaling rate | Low-Speed & Full-Speed | High-Speed | SS (Gen 1) | SS+ (Gen 2) | USB 3.2 Gen 2x2 | USB4 Gen 3×2 | USB4 Gen 4 | ||
| 1.5 Mbit/s & 12 Mbit/s | 480 Mbit/s | 5 Gbit/s | 10 Gbit/s | 20 Gbit/s | 40 Gbit/s | 80 Gbit/s | |||
| Standard A connector | 
|

|

|
— | |||||
| Standard B connector | 
|

|
 [rem 1] [rem 1]
|
— | |||||
| Mini-A connector | — | 
|
— | ||||||
| Mini-B connector | — | 
|
— | ||||||
| Mini-AB connector | — | — | |||||||
| Micro-A connector | — | 
|

|
— | |||||
| Micro-B connector | — | 
|
— | ||||||
| Micro-AB connector | — | 
|

|
— | |||||
| Type-C connector | Backward compatibility given by USB 2.0 implementation |  (Enlarged to show detail) | |||||||
Objectives
The Universal Serial Bus was developed to simplify and improve the interface between personal computers and peripheral devices, such as cell phones, computer accessories, and monitors, when compared with previously existing standard or ad hoc proprietary interfaces.
From the computer user's perspective, the USB interface improves ease of use in several ways:
- The USB interface is self-configuring, eliminating the need for the user to adjust the device's settings for speed or data format, or configure interrupts, input/output addresses, or direct memory access channels.
- USB connectors are standardized at the host, so any peripheral can use most available receptacles.
- USB takes full advantage of the additional processing power that can be economically put into peripheral devices so that they can manage themselves. As such, USB devices often do not have user-adjustable interface settings.
- The USB interface is hot-swappable (devices can be exchanged without rebooting the host computer).
- Small devices can be powered directly from the USB interface, eliminating the need for additional power supply cables.
- Because use of the USB logo is only permitted after compliance testing, the user can have confidence that a USB device will work as expected without extensive interaction with settings and configuration.
- The USB interface defines protocols for recovery from common errors, improving reliability over previous interfaces.
- Installing a device that relies on the USB standard requires minimal operator action. When a user plugs a device into a port on a running computer, it either entirely automatically configures using existing device drivers, or the system prompts the user to locate a driver, which it then installs and configures automatically.
The USB standard also provides multiple benefits for hardware manufacturers and software developers, specifically in the relative ease of implementation:
- The USB standard eliminates the requirement to develop proprietary interfaces to new peripherals.
- The wide range of transfer speeds available from a USB interface suits devices ranging from keyboards and mice up to streaming video interfaces.
- A USB interface can be designed to provide the best available latency for time-critical functions or can be set up to do background transfers of bulk data with little impact on system resources.
- The USB interface is generalized with no signal lines dedicated to only one function of one device.
Limitations
As with all standards, USB possesses multiple limitations to its design:
- USB cables are limited in length, as the standard was intended for peripherals on the same table-top, not between rooms or buildings. However, a USB port can be connected to a gateway that accesses distant devices.
- USB data transfer rates are slower than those of other interconnects such as 100 Gigabit Ethernet.
- USB has a strict tree network topology and master/slave protocol for addressing peripheral devices; those devices cannot interact with one another except via the host, and two hosts cannot communicate over their USB ports directly. Some extension to this limitation is possible through USB On-The-Go in, Dual-Role-Devices and protocol bridge.
- A host cannot broadcast signals to all peripherals at once—each must be addressed individually.
- While converters exist between certain legacy interfaces and USB, they might not provide a full implementation of the legacy hardware. For example, a USB-to-parallel-port converter might work well with a printer, but not with a scanner that requires bidirectional use of the data pins.
For a product developer, using USB requires the implementation of a complex protocol and implies an "intelligent" controller in the peripheral device. Developers of USB devices intended for public sale generally must obtain a USB ID, which requires that they pay a fee to the USB Implementers Forum (USB-IF). Developers of products that use the USB specification must sign an agreement with the USB-IF. Use of the USB logos on the product requires annual fees and membership in the organization.
History


A group of seven companies began the development of USB in 1995: Compaq, DEC, IBM, Intel, Microsoft, NEC, and Nortel. The goal was to make it fundamentally easier to connect external devices to PCs by replacing the multitude of connectors at the back of PCs, addressing the usability issues of existing interfaces, and simplifying software configuration of all devices connected to USB, as well as permitting greater data transfer rates for external devices and Plug and Play features. Ajay Bhatt and his team worked on the standard at Intel; the first integrated circuits supporting USB were produced by Intel in 1995.
USB 1.x
Released in January 1996, USB 1.0 specified signaling rates of 1.5 Mbit/s (Low Bandwidth or Low Speed) and 12 Mbit/s (Full Speed). It did not allow for extension cables, due to timing and power limitations. Few USB devices made it to the market until USB 1.1 was released in August 1998. USB 1.1 was the earliest revision that was widely adopted and led to what Microsoft designated the "Legacy-free PC".
Neither USB 1.0 nor 1.1 specified a design for any connector smaller than the standard type A or type B. Though many designs for a miniaturized type B connector appeared on many peripherals, conformity to the USB 1.x standard was hampered by treating peripherals that had miniature connectors as though they had a tethered connection (that is: no plug or receptacle at the peripheral end). There was no known miniature type A connector until USB 2.0 (revision 1.01) introduced one.
USB 2.0


USB 2.0 was released in April 2000, adding a higher maximum signaling rate of 480 Mbit/s (maximum theoretical data throughput 53 MByte/s) named High Speed or High Bandwidth, in addition to the USB 1.x Full Speed signaling rate of 12 Mbit/s (maximum theoretical data throughput 1.2 MByte/s).
Modifications to the USB specification have been made via engineering change notices (ECNs). The most important of these ECNs are included into the USB 2.0 specification package available from USB.org:
- Mini-A and Mini-B Connector
- Micro-USB Cables and Connectors Specification 1.01
- InterChip USB Supplement
- On-The-Go Supplement 1.3 USB On-The-Go makes it possible for two USB devices to communicate with each other without requiring a separate USB host
- Battery Charging Specification 1.1 Added support for dedicated chargers, host chargers behavior for devices with dead batteries
- Battery Charging Specification 1.2: with increased current of 1.5 A on charging ports for unconfigured devices, allowing High Speed communication while having a current up to 1.5 A
- Link Power Management Addendum ECN, which adds a sleep power state
USB 3.x

The USB 3.0 specification was released on 12 November 2008, with its management transferring from USB 3.0 Promoter Group to the USB Implementers Forum (USB-IF) and announced on 17 November 2008 at the SuperSpeed USB Developers Conference.
USB 3.0 adds a SuperSpeed operation mode, with associated backward-compatible plugs, receptacles, and cables. SuperSpeed plugs and receptacles are identified with a distinct logo and blue inserts in standard format receptacles.
The SuperSpeed bus provides for an operation mode at a rate of 5.0 Gbit/s, in addition to the three existing operation modes. Its efficiency is dependent on a number of factors including physical symbol encoding and link level overhead. At a 5 Gbit/s signaling rate with 8b/10b encoding, each byte needs 10 bits to transmit, so the raw throughput is 500 MB/s. When flow control, packet framing and protocol overhead are considered, it is realistic for 400 MB/s (3.2 Gbit/s) or more to transmit to an application. Communication is full-duplex in SuperSpeed operation mode; earlier modes are half-duplex, arbitrated by the host.

Low-power and high-power devices remain operational with this standard, but devices using SuperSpeed can take advantage of increased available current of between 150 mA and 900 mA, respectively.
USB 3.1, released in July 2013, has two variants. The first one preserves USB 3.0's SuperSpeed operation mode and is labeled USB 3.1 Gen 1, and the second version introduces a new SuperSpeed+ operation mode under the label of USB 3.1 Gen 2. SuperSpeed+ doubles the maximum data signaling rate to 10 Gbit/s, while reducing line encoding overhead to just 3% by changing the encoding scheme to 128b/132b.
USB 3.2, released in September 2017, preserves existing USB 3.1 SuperSpeed and SuperSpeed+ operation modes but introduces two new SuperSpeed+ operation modes with the new USB-C Fabrics with signaling rates of 10 and 20 Gbit/s (1.25 and 2.5 GB/s). The increase in bandwidth is a result of multi-lane operation over existing wires that were intended for flip-flop capabilities of the USB-C connector.
USB 3.0 also introduced the USB Attached SCSI protocol (UASP), which provides generally faster transfer speeds than the BOT (Bulk-Only-Transfer) protocol.
Naming scheme
Starting with the USB 3.2 standard, USB-IF introduced a new naming scheme. To help companies with branding of the different operation modes, USB-IF recommended branding the 5, 10, and 20 Gbit/s operation modes as SuperSpeed USB 5Gbps, SuperSpeed USB 10Gbps, and SuperSpeed USB 20Gbps, respectively. As of September 2022, this naming scheme is deprecated.
USB4
The USB4 specification was released on 29 August 2019 by the USB Implementers Forum.
USB4 is based on the Thunderbolt 3 protocol. It supports 40 Gbit/s throughput, is compatible with Thunderbolt 3, and backward compatible with USB 3.2 and USB 2.0. The architecture defines a method to share a single high-speed link with multiple end device types dynamically that best serves the transfer of data by type and application.
The USB4 specification states that the following technologies shall be supported by USB4:
| Connection | Mandatory for | Remarks | ||
|---|---|---|---|---|
| host | hub | device | ||
| USB 2.0 (480 Mbit/s) | Yes | Yes | Yes | Contrary to other functions—which use the multiplexing of high-speed links—USB 2.0 over USB-C utilizes its own differential pair of wires. |
| Tunneled USB 3.2 Gen 2x1 (10 Gbit/s) | Yes | Yes | No |
|
| Tunneled USB 3.2 Gen 2x2 (20 Gbit/s) | No | No | No |
|
| Tunneled USB3 Gen T (5-80 Gbit/s) | No | No | No | A type of USB3 Tunneling architecture where the Enhanced SuperSpeed protocol is extended to allow operation at the maximum bandwidth available on the USB4 Link. |
| USB4 Gen 2 (10 or 20 Gbit/s) | Yes | Yes | Yes | Either one or two lanes |
| USB4 Gen 3 (20 or 40 Gbit/s) | No | Yes | No | |
| DisplayPort | Yes | Yes | No | The specification requires that hosts and hubs support the DisplayPort Alternate Mode. |
| Host-to-Host communications | Yes | Yes | — | A LAN-like connection between two peers. |
| PCI Express | No | Yes | No | The PCI Express function of USB4 replicates the functionality of previous versions of the Thunderbolt specification. |
| Thunderbolt 3 | No | Yes | No | Thunderbolt 3 uses USB-C cables; the USB4 specification allows hosts and devices and requires hubs to support interoperability with the standard using the Thunderbolt 3 Alternate Mode. |
| Other Alternate Modes | No | No | No | USB4 products may optionally offer interoperability with the HDMI, MHL, and VirtualLink Alternate Modes. |
During CES 2020, USB-IF and Intel stated their intention to allow USB4 products that support all the optional functionality as Thunderbolt 4 products. The first products compatible with USB4 are expected to be Intel's Tiger Lake series and AMD's Zen 3 series of CPU, released in 2020.
The USB4 2.0 specification was released on 1 September 2022 by the USB Implementers Forum.
September 2022 naming scheme

(A mix of USB specifications and their marketing names are being displayed, because specifications are sometimes wrongly used as marketing names)[disputed (for: USB4 20Gbps does not exist; USB4 2x2 is not interchangeable with USB 3.2 2x2 as indicated by the logo; logos for USB 3.x and USB are different) ]
Because of the previous confusing naming schemes, USB-IF decided to change it once again. As of 2 September 2022, marketing names follow the syntax "USB XGbps", where X is the speed of transfer in Gb/s. Overview of the updated names and logos can be seen in the adjacent table.
The operation modes USB 3.2 Gen 2x2 and USB4 Gen 2x2 – or: USB 3.2 Gen 2x1 and USB4 Gen 2x1 – are not interchangeable or compatible; all participating controllers must operate with the same mode.
Version history
Release versions
| Name | Release date | Maximum signaling rate | Note |
|---|---|---|---|
| USB 0.7 | November 1994 | ? | Pre-release |
| USB 0.8 | December 1994 | ? | Pre-release |
| USB 0.9 | April 1995 | 12 Mbit/s : Full Speed (FS) | Pre-release |
| USB 0.99 | August 1995 | ? | Pre-release |
| USB 1.0-RC | November 1995 | ? | Release Candidate |
| USB 1.0 | January 1996 | 1.5 Mbit/s : Low Speed (LS) 12 Mbit/s : Full Speed (FS) |
|
| USB 1.1 | August 1998 |
| |
| USB 2.0 | April 2000 | 480 Mbit/s : High Speed (HS) |
|
| USB 3.0 | November 2008 | 5 Gbit/s : SuperSpeed (SS) | Also referred to as USB 3.1 Gen 1 and USB 3.2 Gen 1×1. |
| USB 3.1 | July 2013 | 10 Gbit/s : SuperSpeed+ (SS+) | Includes new USB 3.1 Gen 2, also named USB 3.2 Gen 2×1 in later specification. |
| USB 3.2 | August 2017 | 20 Gbit/s : SuperSpeed+ two-lane | Includes new USB 3.2 Gen 1×2 and Gen 2×2 multi-link modes. Requires USB-C Fabrics. |
| USB4 | August 2019 | 40 Gbit/s : two-lane | Includes new USB4 Gen 2×2 (64b/66b encoding) and Gen 3×2 (128b/132b encoding) modes and introduces USB4 routing for tunneling of USB 3.2, DisplayPort 1.4a and PCI Express traffic and host-to-host transfers, based on the Thunderbolt 3 protocol; requires USB-C Fabrics. |
| USB4 2.0 | September 2022 | 120 Gbit/s | Includes new 80 and 120 Gbit/s modes over type C connector. Requires USB-C Fabrics. |
| Release name | Release date | Max. power | Note |
|---|---|---|---|
| USB Battery Charging Rev. 1.0 | 2007-03-08 | 7.5 W (5 V, 1.5 A) |
|
| USB Battery Charging Rev. 1.1 | 2009-04-15 | 7.5 W (5 V, 1.5 A) | Page 28, Table 5–2, but with limitation on paragraph 3.5. In ordinary USB 2.0's standard-A port, 1.5 A only. |
| USB Battery Charging Rev. 1.2 | 2010-12-07 | 7.5 W (5 V, 1.5 A) |
|
| USB Power Delivery Rev. 1.0 (V. 1.0) | 2012-07-05 | 100 W (20 V, 5 A) | Using FSK protocol over bus power (VBUS) |
| USB Power Delivery Rev. 1.0 (V. 1.3) | 2014-03-11 | 100 W (20 V, 5 A) |
|
| USB Type-C Rev. 1.0 | 2014-08-11 | 15 W (5 V, 3 A) | New connector and cable specification |
| USB Power Delivery Rev. 2.0 (V. 1.0) | 2014-08-11 | 100 W (20 V, 5 A) | Using BMC protocol over communication channel (CC) on USB-C cables. |
| USB Type-C Rev. 1.1 | 2015-04-03 | 15 W (5 V, 3 A) |
|
| USB Power Delivery Rev. 2.0 (V. 1.1) | 2015-05-07 | 100 W (20 V, 5 A) |
|
| USB Type-C Rev. 1.2 | 2016-03-25 | 15 W (5 V, 3 A) |
|
| USB Power Delivery Rev. 2.0 (V. 1.2) | 2016-03-25 | 100 W (20 V, 5 A) |
|
| USB Power Delivery Rev. 2.0 (V. 1.3) | 2017-01-12 | 100 W (20 V, 5 A) |
|
| USB Power Delivery Rev. 3.0 (V. 1.1) | 2017-01-12 | 100 W (20 V, 5 A) |
|
| USB Type-C Rev. 1.3 | 2017-07-14 | 15 W (5 V, 3 A) |
|
| USB Power Delivery Rev. 3.0 (V. 1.2) | 2018-06-21 | 100 W (20 V, 5 A) |
|
| USB Type-C Rev. 1.4 | 2019-03-29 | 15 W (5 V, 3 A) |
|
| USB Type-C Rev. 2.0 | 2019-08-29 | 15 W (5 V, 3 A) | Enabling USB4 over USB Type-C connectors and cables. |
| USB Power Delivery Rev. 3.0 (V. 2.0) | 2019-08-29 | 100 W (20 V, 5 A) |
|
| USB Power Delivery Rev. 3.1 (V. 1.0) | 2021-05-24 | 240 W (48 V, 5 A) |
|
| USB Type-C Rev. 2.1 | 2021-05-25 | 15 W (5 V, 3 A) | |
| USB Power Delivery Rev. 3.1 (V. 1.1) | 2021-07-06 | 240 W (48 V, 5 A) |
|
| USB Power Delivery Rev. 3.1 (V. 1.2) | 2021-10-26 | 240 W (48 V, 5 A) | Including errata through October 2021
This version incorporates the following ECNs:
|
System design
A USB system consists of a host with one or more downstream ports, and multiple peripherals, forming a tiered-star topology. Additional USB hubs may be included, allowing up to five tiers. A USB host may have multiple controllers, each with one or more ports. Up to 127 devices may be connected to a single host controller. USB devices are linked in series through hubs. The hub built into the host controller is called the root hub.
A USB device may consist of several logical sub-devices that are referred to as device functions. A composite device may provide several functions, for example, a webcam (video device function) with a built-in microphone (audio device function). An alternative to this is a compound device, in which the host assigns each logical device a distinct address and all logical devices connect to a built-in hub that connects to the physical USB cable.

USB device communication is based on pipes (logical channels). A pipe is a connection from the host controller to a logical entity within a device, called an endpoint. Because pipes correspond to endpoints, the terms are sometimes used interchangeably. Each USB device can have up to 32 endpoints (16 in and 16 out), though it is rare to have so many. Endpoints are defined and numbered by the device during initialization (the period after physical connection called "enumeration") and so are relatively permanent, whereas pipes may be opened and closed.
There are two types of pipe: stream and message.
- A message pipe is bi-directional and is used for control transfers. Message pipes are typically used for short, simple commands to the device, and for status responses from the device, used, for example, by the bus control pipe number 0.
- A stream pipe is a uni-directional pipe connected to a uni-directional endpoint that transfers data using an isochronous, interrupt, or bulk transfer:
- Isochronous transfers
- At some guaranteed data rate (for fixed-bandwidth streaming data) but with possible data loss (e.g., realtime audio or video)
- Interrupt transfers
- Devices that need guaranteed quick responses (bounded latency) such as pointing devices, mice, and keyboards
- Bulk transfers
- Large sporadic transfers using all remaining available bandwidth, but with no guarantees on bandwidth or latency (e.g., file transfers)
When a host starts a data transfer, it sends a TOKEN packet containing an endpoint specified with a tuple of (device_address, endpoint_number). If the transfer is from the host to the endpoint, the host sends an OUT packet (a specialization of a TOKEN packet) with the desired device address and endpoint number. If the data transfer is from the device to the host, the host sends an IN packet instead. If the destination endpoint is a uni-directional endpoint whose manufacturer's designated direction does not match the TOKEN packet (e.g. the manufacturer's designated direction is IN while the TOKEN packet is an OUT packet), the TOKEN packet is ignored. Otherwise, it is accepted and the data transaction can start. A bi-directional endpoint, on the other hand, accepts both IN and OUT packets.

Endpoints are grouped into interfaces and each interface is associated with a single device function. An exception to this is endpoint zero, which is used for device configuration and is not associated with any interface. A single device function composed of independently controlled interfaces is called a composite device. A composite device only has a single device address because the host only assigns a device address to a function.
When a USB device is first connected to a USB host, the USB device enumeration process is started. The enumeration starts by sending a reset signal to the USB device. The signaling rate of the USB device is determined during the reset signaling. After reset, the USB device's information is read by the host and the device is assigned a unique 7-bit address. If the device is supported by the host, the device drivers needed for communicating with the device are loaded and the device is set to a configured state. If the USB host is restarted, the enumeration process is repeated for all connected devices.
The host controller directs traffic flow to devices, so no USB device can transfer any data on the bus without an explicit request from the host controller. In USB 2.0, the host controller polls the bus for traffic, usually in a round-robin fashion. The throughput of each USB port is determined by the slower speed of either the USB port or the USB device connected to the port.
High-speed USB 2.0 hubs contain devices called transaction translators that convert between high-speed USB 2.0 buses and full and low speed buses. There may be one translator per hub or per port.
Because there are two separate controllers in each USB 3.0 host, USB 3.0 devices transmit and receive at USB 3.0 signaling rates regardless of USB 2.0 or earlier devices connected to that host. Operating signaling rates for earlier devices are set in the legacy manner.
Device classes
The functionality of a USB device is defined by a class code sent to a USB host. This allows the host to load software modules for the device and to support new devices from different manufacturers.
Device classes include:
| Class | Usage | Description | Examples, or exception |
|---|---|---|---|
| 00h | Device | Unspecified | Device class is unspecified, interface descriptors are used to determine needed drivers |
| 01h | Interface | Audio | Speaker, microphone, sound card, MIDI |
| 02h | Both | Communications and CDC control | UART and RS-232 serial adapter, Modem, Wi-Fi adapter, Ethernet adapter. Used together with class 0Ah (CDC-Data) below |
| 03h | Interface | Human interface device (HID) | Keyboard, mouse, joystick |
| 05h | Interface | Physical interface device (PID) | Force feedback joystick |
| 06h | Interface | Media (PTP/MTP) | Scanner, Camera |
| 07h | Interface | Printer | Laser printer, inkjet printer, CNC machine |
| 08h | Interface | USB mass storage, USB Attached SCSI | USB flash drive, memory card reader, digital audio player, digital camera, external drive |
| 09h | Device | USB hub | High speed USB hub |
| 0Ah | Interface | CDC-Data | Used together with class 02h (Communications and CDC Control) above |
| 0Bh | Interface | Smart Card | USB smart card reader |
| 0Dh | Interface | Content security | Fingerprint reader |
| 0Eh | Interface | Video | Webcam |
| 0Fh | Interface | Personal healthcare device class (PHDC) | Pulse monitor (watch) |
| 10h | Interface | Audio/Video (AV) | Webcam, TV |
| 11h | Device | Billboard | Describes USB-C alternate modes supported by device |
| DCh | Both | Diagnostic device | USB compliance testing device |
| E0h | Interface | Wireless Controller | Bluetooth adapter, Microsoft RNDIS |
| EFh | Both | Miscellaneous | ActiveSync device |
| FEh | Interface | Application-specific | IrDA Bridge, Test & Measurement Class (USBTMC), USB DFU (Device Firmware Upgrade) |
| FFh | Both | Vendor-specific | Indicates that a device needs vendor-specific drivers |
USB mass storage / USB drive


The USB mass storage device class (MSC or UMS) standardizes connections to storage devices. At first intended for magnetic and optical drives, it has been extended to support flash drives and SD card readers. The ability to boot a write-locked SD card with a USB adapter is particularly advantageous for maintaining the integrity and non-corruptible, pristine state of the booting medium.
Though most personal computers since early 2005 can boot from USB mass storage devices, USB is not intended as a primary bus for a computer's internal storage. However, USB has the advantage of allowing hot-swapping, making it useful for mobile peripherals, including drives of various kinds.
Several manufacturers offer external portable USB hard disk drives, or empty enclosures for disk drives. These offer performance comparable to internal drives, limited by the number and types of attached USB devices, and by the upper limit of the USB interface. Other competing standards for external drive connectivity include eSATA, ExpressCard, FireWire (IEEE 1394), and most recently Thunderbolt.
Another use for USB mass storage devices is the portable execution of software applications (such as web browsers and VoIP clients) with no need to install them on the host computer.
Media Transfer Protocol
Media Transfer Protocol (MTP) was designed by Microsoft to give higher-level access to a device's filesystem than USB mass storage, at the level of files rather than disk blocks. It also has optional DRM features. MTP was designed for use with portable media players, but it has since been adopted as the primary storage access protocol of the Android operating system from the version 4.1 Jelly Bean as well as Windows Phone 8 (Windows Phone 7 devices had used the Zune protocol – an evolution of MTP). The primary reason for this is that MTP does not require exclusive access to the storage device the way UMS does, alleviating potential problems should an Android program request the storage while it is attached to a computer. The main drawback is that MTP is not as well supported outside of Windows operating systems.
Human interface devices
A USB mouse or keyboard can usually be used with older computers that have PS/2 ports with the aid of a small USB-to-PS/2 adapter. For mice and keyboards with dual-protocol support, a passive adapter that contains no logic circuitry may be used: the USB hardware in the keyboard or mouse is designed to detect whether it is connected to a USB or PS/2 port, and communicate using the appropriate protocol. Active converters that connect USB keyboards and mice (usually one of each) to PS/2 ports also exist.
Device Firmware Upgrade mechanism
Device Firmware Upgrade (DFU) is a vendor- and device-independent mechanism for upgrading the firmware of USB devices with improved versions provided by their manufacturers, offering (for example) a way to deploy firmware bug fixes. During the firmware upgrade operation, USB devices change their operating mode effectively becoming a PROM programmer. Any class of USB device can implement this capability by following the official DFU specifications.
DFU can also give the user the freedom to flash USB devices with alternative firmware. One consequence of this is that USB devices after being re-flashed may act as various unexpected device types. For example, a USB device that the seller intends to be just a flash drive can "spoof" an input device like a keyboard. See BadUSB.
Audio streaming
The USB Device Working Group has laid out specifications for audio streaming, and specific standards have been developed and implemented for audio class uses, such as microphones, speakers, headsets, telephones, musical instruments, etc. The working group has published three versions of audio device specifications: USB Audio 1.0, 2.0, and 3.0, referred to as "UAC" or "ADC".
UAC 3.0 primarily introduces improvements for portable devices, such as reduced power usage by bursting the data and staying in low power mode more often, and power domains for different components of the device, allowing them to be shut down when not in use.
UAC 2.0 introduced support for High Speed USB (in addition to Full Speed), allowing greater bandwidth for multi-channel interfaces, higher sample rates, lower inherent latency, and 8× improvement in timing resolution in synchronous and adaptive modes. UAC2 also introduced the concept of clock domains, which provides information to the host about which input and output terminals derive their clocks from the same source, as well as improved support for audio encodings like DSD, audio effects, channel clustering, user controls, and device descriptions.
UAC 1.0 devices are still common, however, due to their cross-platform driverless compatibility, and also partly due to Microsoft's failure to implement UAC 2.0 for over a decade after its publication, having finally added support to Windows 10 through the Creators Update on 20 March 2017. UAC 2.0 is also supported by macOS, iOS, and Linux, however Android only implements a subset of the UAC 1.0 specification.
USB provides three isochronous (fixed-bandwidth) synchronization types, all of which are used by audio devices:
- Asynchronous – The ADC or DAC are not synced to the host computer's clock at all, operating off a free-running clock local to the device.
- Synchronous – The device's clock is synced to the USB start-of-frame (SOF) or Bus Interval signals. For instance, this can require syncing an 11.2896 MHz clock to a 1 kHz SOF signal, a large frequency multiplication.e amount of data sent per frame by the host.
While the USB spec originally described asynchronous mode being used in "low cost speakers" and adaptive mode in "high-end digital speakers", the opposite perception exists in the hi-fi world, where asynchronous mode is advertised as a feature, and adaptive/synchronous modes have a bad reputation. In reality, all types can be high-quality or low-quality, depending on the quality of their engineering and the application. Asynchronous has the benefit of being untied from the computer's clock, but the disadvantage of requiring sample rate conversion when combining multiple sources.
Connectors
The connectors the USB committee specifies support a number of USB's underlying goals, and reflect lessons learned from the many connectors the computer industry has used. The female connector mounted on the host or device is called the receptacle, and the male connector attached to the cable is called the plug. The official USB specification documents also periodically define the term male to represent the plug, and female to represent the receptacle.
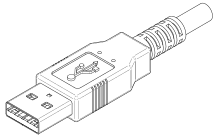
The design is intended to make it difficult to insert a USB plug into its receptacle incorrectly. The USB specification requires that the cable plug and receptacle be marked so the user can recognize the proper orientation. The USB-C plug however is reversible. USB cables and small USB devices are held in place by the gripping force from the receptacle, with no screws, clips, or thumb-turns as some connectors use.
The different A and B plugs prevent accidentally connecting two power sources. However, some of this directed topology is lost with the advent of multi-purpose USB connections (such as USB On-The-Go in smartphones, and USB-powered Wi-Fi routers), which require A-to-A, B-to-B, and sometimes Y/splitter cables.
USB connector types multiplied as the specification progressed. The original USB specification detailed standard-A and standard-B plugs and receptacles. The connectors were different so that users could not connect one computer receptacle to another. The data pins in the standard plugs are recessed compared to the power pins, so that the device can power up before establishing a data connection. Some devices operate in different modes depending on whether the data connection is made. Charging docks supply power and do not include a host device or data pins, allowing any capable USB device to charge or operate from a standard USB cable. Charging cables provide power connections, but not data. In a charge-only cable, the data wires are shorted at the device end, otherwise the device may reject the charger as unsuitable.
Cabling

The USB 1.1 standard specifies that a standard cable can have a maximum length of 5 meters (16 ft 5 in) with devices operating at full speed (12 Mbit/s), and a maximum length of 3 meters (9 ft 10 in) with devices operating at low speed (1.5 Mbit/s).
USB 2.0 provides for a maximum cable length of 5 meters (16 ft 5 in) for devices running at high speed (480 Mbit/s).
The USB 3.0 standard does not directly specify a maximum cable length, requiring only that all cables meet an electrical specification: for copper cabling with AWG 26 wires the maximum practical length is 3 meters (9 ft 10 in).
USB bridge cables
USB bridge cables, or data transfer cables can be found within the market, offering direct PC to PC connections. A bridge cable is a special cable with a chip and active electronics in the middle of the cable. The chip in the middle of the cable acts as a peripheral to both computers and allows for peer-to-peer communication between the computers. The USB bridge cables are used to transfer files between two computers via their USB ports.
Popularized by Microsoft as Windows Easy Transfer, the Microsoft utility used a special USB bridge cable to transfer personal files and settings from a computer running an earlier version of Windows to a computer running a newer version. In the context of the use of Windows Easy Transfer software, the bridge cable can sometimes be referenced as Easy Transfer cable.
Many USB bridge / data transfer cables are still USB 2.0, but there are also a number of USB 3.0 transfer cables. Despite USB 3.0 being 10 times faster than USB 2.0, USB 3.0 transfer cables are only 2 - 3 times faster given their design.
The USB 3.0 specification introduced an A-to-A cross-over cable without power for connecting two PCs. These are not meant for data transfer but are aimed at diagnostic uses.
Dual-role USB connections
USB bridge cables have become less important with USB dual-role-device capabilities introduced with the USB 3.1 specification. Under the most recent specifications, USB supports most scenarios connecting systems directly with a Type-C cable. For the capability to work, however, connected systems must support role-switching. Dual-role capabilities requires there be two controllers within the system, as well as a role controller. While this can be expected in a mobile platform such as a tablet or a phone, desktop PCs and laptops often will not support dual roles.
Power
Upstream USB connectors supply power at a nominal 5V DC via the V_BUS pin to downstream USB devices.
Low-power and high-power devices
Low-power devices may draw at most 1-unit load, and all devices must act as low-power devices when starting out as unconfigured. 1 unit load is 100 mA for USB devices up to USB 2.0, while USB 3.0 defines a unit load as 150 mA. Multi-lane operations (USB-C) support low power devices with a unit load of 250 mA.
High-power devices (such as a typical 2.5-inch USB hard disk drive) draw at least 1 unit load and at most 5-unit loads (5x100mA = 500 mA) for devices up to USB 2.0- or 6-unit loads (6x150mA = 900 mA) for SuperSpeed (USB 3.0 and up) devices. Multi-lane operations (USB-C) support high power devices with up to 1500 mA (6x250mA).
| Specification | Current | Voltage | Power (max.) |
|---|---|---|---|
| Low-power device | 100 mA | 5 V | 0.50 W |
| Low-power SuperSpeed (USB 3.0) device | 150 mA | 5 V | 0.75 W |
| High-power device | 500 mA | 5 V | 2.5 W |
| High-power SuperSpeed (USB 3.0) device | 900 mA | 5 V | 4.5 W |
| Multi-lane SuperSpeed (USB 3.2 Gen x2) device | 1.5 A | 5 V | 7.5 W |
| Battery Charging (BC) 1.1 | 1.5 A | 5 V | 7.5 W |
| Battery Charging (BC) 1.2 | 1.5 A | 5 V | 7.5 W |
| USB-C (multi-lane) | 1.5 A | 5 V | 7.5 W |
| 3 A | 5 V | 15 W | |
| Power Delivery 1.0/2.0/3.0 Type-C | 5 A | 20 V | 100 W |
| Power Delivery 3.1 Type-C | 5 A | 48 V | 240 W |
|
To recognize Battery Charging mode, a dedicated charging port places a resistance not exceeding 200 Ω across the D+ and D− terminals. Shorted or near-shorted data lanes with less than 200 Ω of resistance across the "D+" and "D−" terminals signify a dedicated charging port (DCP) with indefinite charging rates.
In addition to standard USB, there is a proprietary high-powered system known as PoweredUSB, developed in the 1990s, and mainly used in point-of-sale terminals such as cash registers.
Signaling
USB signals are transmitted using differential signaling on twisted-pair data wires with 90 Ω ± 15% characteristic impedance. USB 2.0 and earlier specifications define a single pair in half-duplex (HDx). USB 3.0 and later specifications define one dedicated pair for USB 2.0 compatibility and two or four pairs for data transfer: two pairs in full-duplex (FDx) for single lane variants require SuperSpeed connectors; four pairs in full-duplex for two lane (×2) variants require USB-C connectors. USB4 Gen 4 requires the use of all four pairs but allow for asymmetrical pairs configuration, in this case one lane is used for the upstream data and the other tree for the downstream data or vice-versa. USB4 Gen 4 use pulse amplitude modulation on 3 levels, providing a trit of information every baud transmited, the transmission frequency of 12,8GHz translate to a transmission rate of 25,6 Gigabaud and the 11 bit to 7 trit translation provides a theorical maximum transmision speed just over 40,2 Gbit/s.
| Operation mode | Old name | Introduced in | Encoding | Data wire pairs | Nominal rate | USB-IF marketing
name |
Logo |
|---|---|---|---|---|---|---|---|
| Low-Speed |
|
USB 1.0 | NRZI | 1 HDx | 1.5 Mbit/s | Low-Speed USB | |
| Full-Speed | 12 Mbit/s | ||||||
| High-Speed | USB 2.0 | 480 Mbit/s | Hi-Speed USB | ||||
| USB 3.2 Gen 1×1 | USB 3.0, USB 3.1 Gen 1 |
USB 3.0 | 8b/10b | 2 FDx (+ 1 HDx) | 5 Gbit/s | SuperSpeed USB 5Gbps | |
| USB 3.2 Gen 2×1 | USB 3.1 Gen 2 | USB 3.1 | 128b/132b | 2 FDx (+ 1 HDx) | 10 Gbit/s | SuperSpeed USB 10Gbps | |
| USB 3.2 Gen 1×2 |
|
USB 3.2 | 8b/10b | 4 FDx (+ 1 HDx) | 10 Gbit/s | — | |
| USB 3.2 Gen 2×2 | 128b/132b | 4 FDx (+ 1 HDx) | 20 Gbit/s | SuperSpeed USB 20Gbps | |||
| USB4 Gen 2×1 | USB4 | 64b/66b | 2 FDx (+ 1 HDx) | 10 Gbit/s | — | ||
| USB4 Gen 2×2 | 64b/66b | 4 FDx (+ 1 HDx) | 20 Gbit/s | USB4 20Gbps | |||
| USB4 Gen 3×1 | 128b/132b | 2 FDx (+ 1 HDx) | 20 Gbit/s | — | |||
| USB4 Gen 3×2 | 128b/132b | 4 FDx (+ 1 HDx) | 40 Gbit/s | USB4 40Gbps | |||
| USB4 Gen 4 |
|
USB4 version 2.0 | PAM-3 11b/7t | 4 FDx (+ 1 HDx) | 80 Gbit/s | USB4 80Gbps |
|
| 40 Gbit/s up
120 Gbit/s down |
| ||||||
| 120 Gbit/s up
40 Gbit/s down | |||||||
- USB4 can use optional Reed–Solomon forward error correction (RS FEC). In this mode, 12 × 16 B (128 bit) symbols are assembled together with 2 B (12 bit + 4 bit reserved) synchronization bits indicating the respective symbol types and 4 B of RS FEC to allow to correct up to 1 B of errors anywhere in the total 198 B block.
- Low-speed (LS) and Full-speed (FS) modes use a single data wire pair, labeled D+ and D−, in half-duplex. Transmitted signal levels are 0.0–0.3 V for logical low, and 2.8–3.6 V for logical high level. The signal lines are not terminated.
- High-speed (HS) uses the same wire pair, but with different electrical conventions. Lower signal voltages of −10 to 10 mV for low and 360 to 440 mV for logical high level, and termination of 45 Ω to ground or 90 Ω differential to match the data cable impedance.
- SuperSpeed (SS) adds two additional pairs of shielded twisted data wires (and new, mostly compatible expanded connectors) besides another grounding wire. These are dedicated to full-duplex SuperSpeed operation. The SuperSpeed link operates independently from USB 2.0 channel and takes a precedence on connection. Link configuration is performed using LFPS (Low Frequency Periodic Signaling, approximately at 20 MHz frequency), and electrical features include voltage de-emphasis at transmitter side, and adaptive linear equalization on receiver side to combat electrical losses in transmission lines, and thus the link introduces the concept of link training.
- SuperSpeed+ (SS+) uses a new coding scheme with an increased signaling rate (Gen 2×1 mode) and/or the additional lane of USB-C (Gen 1×2 and Gen 2×2 modes).
A USB connection is always between a host or hub at the A connector (or USB-C) end, and a device or hub's "upstream" port at the other end.
Protocol layer
During USB communication, data is transmitted as packets. Initially, all packets are sent from the host via the root hub, and possibly more hubs, to devices. Some of those packets direct a device to send some packets in reply.
Transactions
The basic transactions of USB are:
- OUT transaction
- IN transaction
- SETUP transaction
- Control transfer exchange
Related standards

Media Agnostic USB
The USB Implementers Forum introduced the Media Agnostic USB (MA-USB) v.1.0 wireless communication standard based on the USB protocol on 29 July 2015. Wireless USB is a cable-replacement technology, and uses ultra-wideband wireless technology for data rates of up to 480 Mbit/s.
The USB-IF used WiGig Serial Extension v1.2 specification as its initial foundation for the MA-USB specification and is compliant with SuperSpeed USB (3.0 and 3.1) and Hi-Speed USB (USB 2.0). Devices that use MA-USB will be branded as 'Powered by MA-USB', provided the product qualifies its certification program.
InterChip USB
InterChip USB is a chip-to-chip variant that eliminates the conventional transceivers found in normal USB. The HSIC physical layer uses about 50% less power and 75% less board area compared to USB 2.0. It is an alternative standard to SPI and I2C.
USB-C
USB-C (officially USB Type-C) is a standard that defines a new connector, and several new connection features. Among them it supports Alternate Mode, which allows transporting other protocols via the USB-C connector and cable. This is commonly used to support the DisplayPort or HDMI protocols, which allows connecting a display, such as a computer monitor or television set, via USB-C.
All other connectors are not capable of two-lane operations (Gen 1x2 and Gen 2x2) in USB 3.2, but can be used for one-lane operations (Gen1x1 and Gen2x1).
DisplayLink
DisplayLink is a technology which allows multiple displays to be connected to a computer via USB. It was introduced around 2006, and before the advent of Alternate Mode over USB-C it was the only way to connect displays via USB. It is a proprietary technology, not standardized by the USB Implementers Forum and typically requires a separate device driver on the computer.
Comparisons with other connection methods
FireWire (IEEE 1394)
At first, USB was considered a complement to FireWire (IEEE 1394) technology, which was designed as a high-bandwidth serial bus that efficiently interconnects peripherals such as disk drives, audio interfaces, and video equipment. In the initial design, USB operated at a far lower data rate and used less sophisticated hardware. It was suitable for small peripherals such as keyboards and pointing devices.
The most significant technical differences between FireWire and USB include:
- USB networks use a tiered-star topology, while IEEE 1394 networks use a tree topology.
- USB 1.0, 1.1, and 2.0 use a "speak-when-spoken-to" protocol, meaning that each peripheral communicates with the host when the host specifically requests it to communicate. USB 3.0 allows for device-initiated communications towards the host. A FireWire device can communicate with any other node at any time, subject to network conditions.
- A USB network relies on a single host at the top of the tree to control the network. All communications are between the host and one peripheral. In a FireWire network, any capable node can control the network.
- USB runs with a 5 V power line, while FireWire supplies 12 V and theoretically can supply up to 30 V.
- Standard USB hub ports can provide from the typical 500 mA/2.5 W of current, only 100 mA from non-hub ports. USB 3.0 and USB On-The-Go supply 1.8 A/9.0 W (for dedicated battery charging, 1.5 A/7.5 W full bandwidth or 900 mA/4.5 W high bandwidth), while FireWire can in theory supply up to 60 watts of power, although 10 to 20 watts is more typical.
These and other differences reflect the differing design goals of the two buses: USB was designed for simplicity and low cost, while FireWire was designed for high performance, particularly in time-sensitive applications such as audio and video. Although similar in theoretical maximum signaling rate, FireWire 400 is faster than USB 2.0 high-bandwidth in real-use, especially in high-bandwidth use such as external hard drives. The newer FireWire 800 standard is twice as fast as FireWire 400 and faster than USB 2.0 high-bandwidth both theoretically and practically. However, FireWire's speed advantages rely on low-level techniques such as direct memory access (DMA), which in turn have created opportunities for security exploits such as the DMA attack.
The chipset and drivers used to implement USB and FireWire have a crucial impact on how much of the bandwidth prescribed by the specification is achieved in the real world, along with compatibility with peripherals.
Ethernet
The IEEE 802.3af, 802.3at, and 802.3bt Power over Ethernet (PoE) standards specify more elaborate power negotiation schemes than powered USB. They operate at 48 V DC and can supply more power (up to 12.95 W for 802.3af, 25.5 W for 802.3at aka PoE+, 71 W for 802.3bt aka 4PPoE) over a cable up to 100 meters compared to USB 2.0, which provides 2.5 W with a maximum cable length of 5 meters. This has made PoE popular for VoIP telephones, security cameras, wireless access points, and other networked devices within buildings. However, USB is cheaper than PoE provided that the distance is short and power demand is low.
Ethernet standards require electrical isolation between the networked device (computer, phone, etc.) and the network cable up to 1500 V AC or 2250 V DC for 60 seconds. USB has no such requirement as it was designed for peripherals closely associated with a host computer, and in fact it connects the peripheral and host grounds. This gives Ethernet a significant safety advantage over USB with peripherals such as cable and DSL modems connected to external wiring that can assume hazardous voltages under certain fault conditions.
MIDI
The USB Device Class Definition for MIDI Devices transmits Music Instrument Digital Interface (MIDI) music data over USB. The MIDI capability is extended to allow up to sixteen simultaneous virtual MIDI cables, each of which can carry the usual MIDI sixteen channels and clocks.
USB is competitive for low-cost and physically adjacent devices. However, Power over Ethernet and the MIDI plug standard have an advantage in high-end devices that may have long cables. USB can cause ground loop problems between equipment, because it connects ground references on both transceivers. By contrast, the MIDI plug standard and Ethernet have built-in isolation to 500V or more.
eSATA/eSATAp
The eSATA connector is a more robust SATA connector, intended for connection to external hard drives and SSDs. eSATA's transfer rate (up to 6 Gbit/s) is similar to that of USB 3.0 (up to 5 Gbit/s) and USB 3.1 (up to 10 Gbit/s). A device connected by eSATA appears as an ordinary SATA device, giving both full performance and full compatibility associated with internal drives.
eSATA does not supply power to external devices. This is an increasing disadvantage compared to USB. Even though USB 3.0's 4.5 W is sometimes insufficient to power external hard drives, technology is advancing, and external drives gradually need less power, diminishing the eSATA advantage. eSATAp (power over eSATA; aka ESATA/USB) is a connector introduced in 2009 that supplies power to attached devices using a new, backward compatible, connector. On a notebook eSATAp usually supplies only 5 V to power a 2.5-inch HDD/SSD; on a desktop workstation it can additionally supply 12 V to power larger devices including 3.5-inch HDD/SSD and 5.25-inch optical drives.
eSATAp support can be added to a desktop machine in the form of a bracket connecting the motherboard SATA, power, and USB resources.
eSATA, like USB, supports hot plugging, although this might be limited by OS drivers and device firmware.
Thunderbolt
Thunderbolt combines PCI Express and Mini DisplayPort into a new serial data interface. Original Thunderbolt implementations have two channels, each with a transfer speed of 10 Gbit/s, resulting in an aggregate unidirectional bandwidth of 20 Gbit/s.
Thunderbolt 2 uses link aggregation to combine the two 10 Gbit/s channels into one bidirectional 20 Gbit/s channel.
Thunderbolt 3 uses USB-C. Thunderbolt 3 has two physical 20 Gbit/s bi-directional channels, aggregated to appear as a single logical 40 Gbit/s bi-directional channel. Thunderbolt 3 controllers can incorporate a USB 3.1 Gen 2 controller to provide compatibility with USB devices. They are also capable of providing DisplayPort alternate mode over the USB-C Fabrics, making a Thunderbolt 3 port a superset of a USB 3.1 Gen 2 port with DisplayPort alternate mode.
DisplayPort Alt Mode 2.0: USB4 supports DisplayPort 2.0 over its alternate mode. DisplayPort 2.0 can support 8K resolution at 60 Hz with HDR10 color. DisplayPort 2.0 can use up to 80 Gbit/s, which is double the amount available to USB data, because it sends all the data in one direction (to the monitor) and can thus use all eight data lanes at once.
After the specification was made royalty-free and custodianship of the Thunderbolt protocol was transferred from Intel to the USB Implementers Forum, Thunderbolt 3 has been effectively implemented in the USB4 specification—with compatibility with Thunderbolt 3 optional but encouraged for USB4 products.
Interoperability
Various protocol converters are available that convert USB data signals to and from other communications standards.
Security threats
Due to the prevalency of the USB standard, there are many exploits using the USB standard. One of the biggest instances of this today is known as the USB Killer, a device which damages devices by sending high voltage pulses across the data lines.
In versions of Microsoft Windows before Windows XP, Windows would automatically run a script (if present) on certain devices via autorun, one of which are USB mass storage devices, which may contain malicious software.





